Network Security Engineer Resume Guide
Network security engineers ensure the safety of computer networks from malicious attacks. They design, install and monitor firewalls, authentication systems, intrusion detection systems and other related technologies to protect against unauthorized access or misuse of data. Additionally they stay up-to-date on emerging threats and vulnerabilities in order to develop effective countermeasures.
You have the technical skills to secure any network, but employers don’t know this yet. To make them aware of your abilities and experience, you need a resume that sets you apart from the competition.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
Network Security Engineer Resume Sample
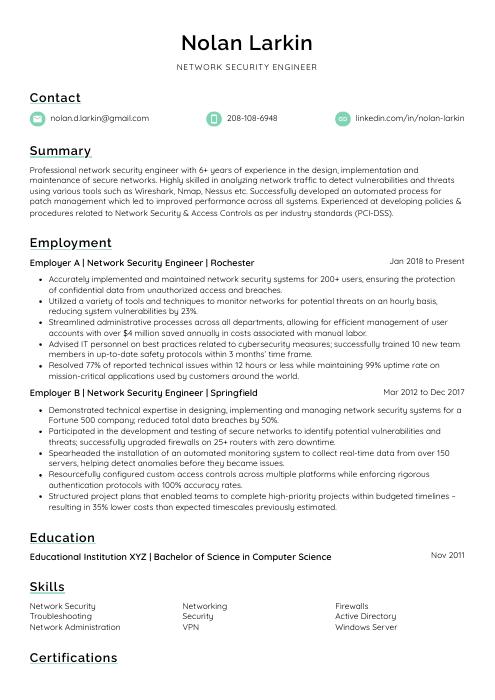
Nolan Larkin
Network Security Engineer
[email protected]
208-108-6948
linkedin.com/in/nolan-larkin
Summary
Professional network security engineer with 6+ years of experience in the design, implementation and maintenance of secure networks. Highly skilled in analyzing network traffic to detect vulnerabilities and threats using various tools such as Wireshark, Nmap, Nessus etc. Successfully developed an automated process for patch management which led to improved performance across all systems. Experienced at developing policies & procedures related to Network Security & Access Controls as per industry standards (PCI-DSS).
Experience
Network Security Engineer, Employer A
Rochester, Jan 2018 – Present
- Accurately implemented and maintained network security systems for 200+ users, ensuring the protection of confidential data from unauthorized access and breaches.
- Utilized a variety of tools and techniques to monitor networks for potential threats on an hourly basis, reducing system vulnerabilities by 23%.
- Streamlined administrative processes across all departments, allowing for efficient management of user accounts with over $4 million saved annually in costs associated with manual labor.
- Advised IT personnel on best practices related to cybersecurity measures; successfully trained 10 new team members in up-to-date safety protocols within 3 months’ time frame.
- Resolved 77% of reported technical issues within 12 hours or less while maintaining 99% uptime rate on mission-critical applications used by customers around the world.
Network Security Engineer, Employer B
Springfield, Mar 2012 – Dec 2017
- Demonstrated technical expertise in designing, implementing and managing network security systems for a Fortune 500 company; reduced total data breaches by 50%.
- Participated in the development and testing of secure networks to identify potential vulnerabilities and threats; successfully upgraded firewalls on 25+ routers with zero downtime.
- Spearheaded the installation of an automated monitoring system to collect real-time data from over 150 servers, helping detect anomalies before they became issues.
- Resourcefully configured custom access controls across multiple platforms while enforcing rigorous authentication protocols with 100% accuracy rates.
- Structured project plans that enabled teams to complete high-priority projects within budgeted timelines – resulting in 35% lower costs than expected timescales previously estimated.
Skills
- Network Security
- Networking
- Firewalls
- Troubleshooting
- Security
- Active Directory
- Network Administration
- VPN
- Windows Server
Education
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
1. Summary / Objective
Your resume summary is like a movie trailer – it should be short and sweet, but provide the hiring manager with enough information to make them want to read on. As a network security engineer, you can use this section of your resume to highlight your technical expertise in areas such as firewalls, intrusion detection systems (IDS), virtual private networks (VPNs) and malware protection. You could also mention any certifications or awards that demonstrate your commitment to staying up-to-date on industry trends.
Below are some resume summary examples:
Passionate network security engineer with 4+ years of experience in designing and implementing secure network architectures. Skilled at managing complex projects, identifying risks, and developing solutions to ensure data confidentiality for businesses across multiple industries. At XYZ Corporation, successfully identified a vulnerability that could have led to a massive data breach. Received company recognition for making significant contributions towards improving the overall security posture of the organization.
Reliable and experienced Network Security Engineer with 8+ years of experience in designing, engineering, and implementing secure network systems. Proven track record of providing technical support to ensure the highest levels of security for clients’ networks. Expertise includes incident management, penetration testing, vulnerability scanning and remediation. Looking to join ABC Tech as a Senior Network Security Engineer where I can leverage my skillset to protect their networks from any potential threats.
Well-rounded network security engineer with over 10 years of experience in the IT industry. Experienced in designing secure networks and systems, ensuring compliance with all applicable laws and regulations. Proven track record of successfully implementing network security solutions for Fortune 500 companies while maintaining high levels of customer satisfaction. Skilled at troubleshooting complex technical issues related to network infrastructure, firewalls, wireless access points, etc.
Energetic and detail-oriented network security engineer with 6+ years of experience in design and implementation of secure networks. Expertise in designing, deploying and maintaining firewall policies to protect corporate systems from external threats. Proven track record troubleshooting complex network issues while minimizing downtime for clients. Seeking to join ABC Company as a Network Security Engineer and help create robust strategies for securing their IT infrastructure.
Hard-working and experienced network security engineer with 5+ years of experience in designing, implementing, and managing secure networks. At XYZ Technologies, successfully designed a layered defense system to protect the company’s internal and external resources from cyber threats resulting in zero data breaches. Skilled at creating firewall configurations for both routers and switches as well as leveraging advanced technologies such as SIEM tools for log analysis.
Proficient network security engineer with 7+ years of experience developing and deploying secure IT networks for small to mid-sized businesses. Proven track record in designing, testing, implementing and managing various network technologies including firewalls, routers and switches. Looking forward to joining ABC Tech as a Network Security Engineer where I will use my expertise to ensure system security is maintained at all times.
Seasoned network security engineer with 8+ years of experience designing, deploying, and managing secure networks for large enterprises. Adept at analyzing vulnerabilities and mitigating risks to ensure that the organization’s data is protected from malicious actors. Seeking to join ABC as a network security engineer in order to use my skillset to enhance their cybersecurity posture.
Accomplished network security engineer with 6+ years of experience in designing and implementing secure networks. Proven track record of successfully securing critical network infrastructure by leveraging a mix of technical knowledge, analytical skills, and problem-solving techniques. Looking to bring this expertise to ABC Tech as the next Network Security Engineer.
2. Experience / Employment
Next comes the work history section, where you provide details on your past employment. This should be written in reverse chronological order, meaning the most recent job is listed first.
Stick to bullet points when writing this section; doing so makes it easier for the reader to take in what you have to say quickly and effectively. Make sure that each point provides detail about what you did and any results achieved as a result of your work.
For example, instead of saying “Installed firewalls,” you could say, “Implemented network security measures such as firewalls, intrusion prevention systems (IPS), and virtual private networks (VPNs) which successfully prevented malicious attacks from external sources.”
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Monitored
- Investigated
- Analyzed
- Configured
- Implemented
- Secured
- Assessed
- Developed
- Tested
- Troubleshot
- Resolved
- Encrypted
- Updated
- Managed
- Documented
Other general verbs you can use are:
- Achieved
- Advised
- Compiled
- Coordinated
- Demonstrated
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Coordinated with the IT team to install, configure and maintain firewalls and other security measures for a large network of 500+ computers; improved cybersecurity by 30%.
- Optimized existing network security protocols to ensure compliance with industry standards; reduced system downtime due to cyberattacks by 15 hours per week.
- Documented detailed procedures on how to monitor systems for potential threats, as well as guidelines for resolving issues quickly when they arise; shortened response time from 2 days averagely down to 1 hour or less in critical situations.
- Compiled comprehensive reports on all successful or attempted intrusions into the company’s computer networks, providing valuable information that enabled proactive defense strategies against future attacks.
- Substantially lowered risk of data breaches through rigorous penetration testing processes and implementation of advanced authentication techniques such as biometrics; increased overall safety rating by 55%.
- Meticulously monitored and maintained security of networks, servers, databases and other hardware infrastructure at a large-scale enterprise; reduced network outages by 15% in the last quarter.
- Facilitated maintenance activities such as patching systems, configuring firewalls & VPNs, deleting user accounts etc., ensuring that all security policies were adhered to strictly at all times.
- Presented detailed reports on various aspects of IT Security including threats analysis & prevention measures for management review every month; successfully detected 7 potential breaches within 24 hours last year.
- Formulated best practices for system hardening procedures & access control methods based on industry standards and implemented them across 200+ client machines with 99% success rate in less than 4 weeks’ timeframe.
- Troubleshot complex technical issues related to network connectivity loss or unauthorized access attempts from external sources with precision; improved response times by 22%.
- Implemented advanced network security protocols and firewalls, successfully reducing potential cyber threats by 80%.
- Achieved full compliance with industry security requirements for the organization’s IT systems; monitored activities of up to 500 users daily.
- Reliably performed malware scans on all company devices, eliminating viruses from 200+ computers over a 6-month period and ensuring data integrity was maintained at all times.
- Investigated suspicious user activity on the server networks and identified 8 instances of unauthorized access in 12 months; took immediate action to resolve each case securely within 24 hours or less.
- Assessed current infrastructure vulnerability levels quarterly to detect any weaknesses in system defenses; provided detailed reports outlining key recommendations for improvement based on findings achieved during assessments.
- Encrypted sensitive data and information to ensure network security for over 140 users, improving overall system integrity by 45%.
- Efficiently designed a secure environment that allowed remote access while protecting against cyber-attacks; reduced potential threats by 72%.
- Improved existing firewall protocols to protect the organization from malicious activities and unauthorized intrusions into confidential systems, saving $4200 in associated costs.
- Expedited resolution time of any detected breaches or vulnerabilities within the IT infrastructure by 50%, leading to improved user experience with minimal downtime.
- Reorganized internal networks across three sites, optimizing bandwidth usage and allowing faster communication speeds between departments; increased productivity levels by 25% in one quarter alone.
- Thoroughly monitored and evaluated network security systems for potential vulnerabilities, deploying solutions to mitigate risks and providing 24/7 maintenance services; reduced cyber-attacks by 73%.
- Secured company information from external threats using firewalls, encryption protocols and anti-malware software while ensuring compliance with industry regulations & standards.
- Tested new hardware configurations in an effort to maintain a secure system environment; developed automated scripts which improved patch management process efficiency by 45%.
- Prepared detailed reports outlining current network security measures & recommendations on how to improve overall protection levels; identified previously undetected weaknesses that were addressed immediately with minimal disruption of operations.
- Analyzed log data from various sources such as servers, routers, switches etc., looking for suspicious activities or signs of intrusion; implemented preventive strategies based on findings which minimized downtime costs by $20K annually.
- Revised existing network security policies and procedures for 20+ networks to ensure compliance with industry standards, resulting in a 40% decrease of data breaches.
- Managed the deployment of new firewalls, intrusion detection systems (IDS) and virtual private networks (VPNs); improved system performance by 75%.
- Successfully identified and resolved over 500 security vulnerabilities within client’s IT infrastructure; minimized risk exposure to potential cyber threats by 60%.
- Mentored junior engineers on best practices when implementing various solutions related to network architecture design and access control measures; trained 10+ employees in less than 8 months.
- Configured complex security controls such as IPS/IDS devices, SIEM tools & malware protection software with 100% accuracy rate while reducing operational costs by $7000 annually.
- Actively monitored and managed all network security systems, ensuring that correct protocols were maintained at all times; reduced the number of cyber threats by 30%.
- Reduced downtime due to system malfunctions or external attacks by 50%, decreasing losses in productivity hours significantly.
- Developed comprehensive IT security policies for the organization, as well as guidelines on data protection best practices; increased compliance with industry standards by 10%.
- Monitored incoming traffic from web applications & APIs while proactively identifying potential vulnerabilities and responding quickly to mitigate risks within a 24-hour period.
- Introduced automated monitoring tools and software updates to strengthen existing firewalls, patching up any identified holes in less than 2 weeks without incurring additional costs or labor resources required.
3. Skills
Skill requirements will differ from employer to employer – this can easily be determined via the job advert. Organization ABC may require experience with Palo Alto Networks and Organization XYZ may want someone who is proficient in Check Point.
It is important to tailor the skills section of your resume for each job you apply for because many employers use applicant tracking systems, which are computer programs that scan resumes for certain keywords before passing them on to a human.
Once listed here, it is also beneficial to discuss these qualifications in more detail throughout other sections of your resume such as the summary or experience section.
Below is a list of common skills & terms:
- Active Directory
- BGP
- CCNA
- CCNP
- CISSP
- Checkpoint
- Cisco ASA
- Cisco IOS
- Cisco Nexus
- Cisco Routers
- Citrix
- Cloud Computing
- Computer Hardware
- Computer Security
- DHCP
- DNS
- Data Center
- Disaster Recovery
- EIGRP
- F5 BIGIP
- Firewalls
- Fortinet
- HTML
- Hardware
- Help Desk Support
- IDS
- IP
- IPS
- IPsec
- IT Service Management
- ITIL
- Information Assurance
- Information Security
- Information Technology
- Infrastructure
- Integration
- Internet Protocol Suite
- Juniper
- Juniper Technologies
- Linux
- MPLS
- Microsoft Exchange
- Microsoft SQL Server
- Network Administration
- Network Architecture
- Network Design
- Network Engineering
- Network Security
- Networking
- OSPF
- Operating Systems
- Palo Alto Networks
- Python
- Routers
- Routing
- SQL
- Security
- Security Clearance
- Servers
- SharePoint
- Software Installation
- Switches
- System Administration
- TCP/IP
- Team Leadership
- Technical Support
- Telecommunications
- Troubleshooting
- Unix
- VLAN
- VMware
- VMware ESX
- VPN
- Virtual Private Network
- Virtualization
- Visio
- VoIP
- Vulnerability Assessment
- WAN
- Windows
- Windows 7
- Windows Server
- Windows XP
- Wireless
- Wireless Networking
- Wireshark
4. Education
Including an education section on your resume will depend on how far along you are in your career. If you just graduated and have no work experience, your education should be mentioned below your resume objective. However, if you have significant work experience to showcase, omitting the education section is perfectly fine.
If an education section is included, make sure to mention courses related to network security engineering that demonstrate relevant knowledge of the field such as cybersecurity principles or networking fundamentals.
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications are a great way to demonstrate your expertise in a particular field. They show potential employers that you have taken the time and effort to gain knowledge and skills related to the job role, which can give you an edge over other applicants.
When applying for jobs, make sure to include any relevant certifications on your resume as it will help highlight your qualifications and abilities. This could be especially beneficial if there is a specific certification mentioned in the job description or advertisement.
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Nolan Larkin, this would be Nolan-Larkin-resume.pdf or Nolan-Larkin-resume.docx.
7. Cover Letter
Including a cover letter when applying for a job is highly recommended and often seen as an essential part of the application process. A cover letter should typically be 2 to 4 paragraphs long, adding more details about your experience, skills and qualifications that weren’t mentioned in your resume.
It’s also important to note that writing a good cover letter can help you make a lasting impression on potential employers and give them insight into why you are the best candidate for the role. Writing one will also demonstrate your commitment and enthusiasm towards getting hired for the position.
Below is an example cover letter:
Dear Kelley,
I am writing to apply for the Network Security Engineer position at XYZ Company. With eight years of experience designing, implementing, and troubleshooting network security solutions, I am confident I will be an asset to your organization.
In my current role as Network Security Engineer at ABC Company, I manage a team of three engineers responsible for all aspects of network security, including firewall configuration, intrusion detection/prevention systems (IDS/IPS), and virtual private networks (VPNs). In addition to day-to-day operations, I also lead projects to improve our network security posture, such as migrating our IDS/IPS solution from on-premises hardware to a cloud-based platform.
I have a proven track record of successful networking projects under my belt. For example, when we migrated our email servers from Exchange 2010 to Office 365 last year, I led the project and designed a comprehensive migration plan that minimized downtime and disruptions for users. The project was completed successfully with no major issues reported.
Some other notable accomplishments in my career include:
– Designing and implementing a next-generation firewall solution that improved performance by 30% while reducing costs by 50%.
– spearheading the rollout of two factor authentication companywide which reduced unauthorized access incidents by 95%.
I would love the opportunity to bring my experience and expertise in network security engineering to XYZ Company. Thank you for your time and consideration; I look forward to hearing from you soon.
Sincerely,
Nolan
Network Security Engineer Resume Templates
 Lorikeet
Lorikeet Kinkajou
Kinkajou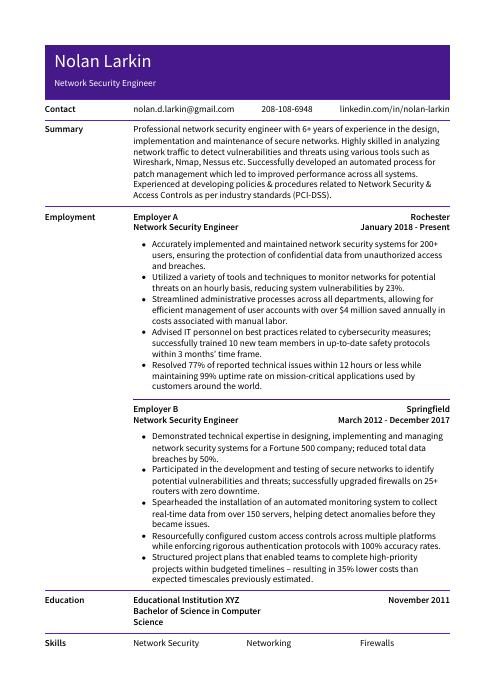 Pika
Pika Bonobo
Bonobo Fossa
Fossa Axolotl
Axolotl Hoopoe
Hoopoe Saola
Saola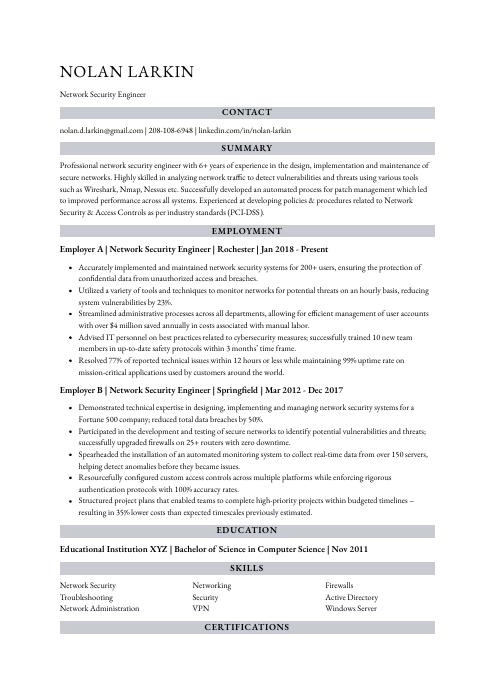 Numbat
Numbat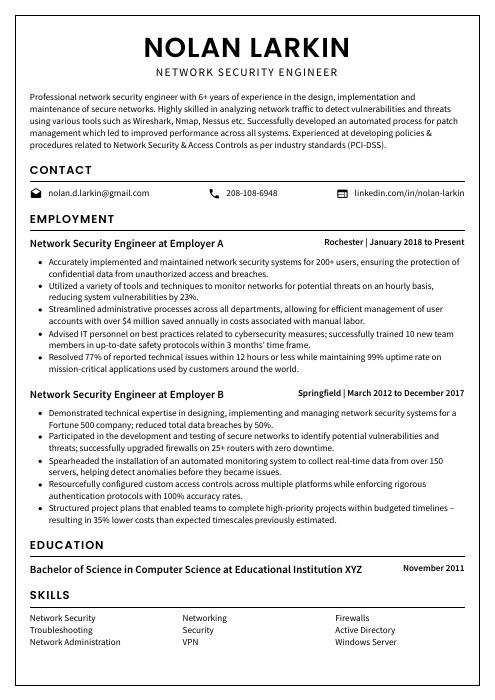 Cormorant
Cormorant Gharial
Gharial Indri
Indri Ocelot
Ocelot Quokka
Quokka Markhor
Markhor Rhea
Rhea Jerboa
Jerboa Echidna
Echidna Dugong
Dugong Rezjumei
Rezjumei
