Information Systems Security Officer Resume Guide
Information Systems Security Officers protect the security of computer systems by monitoring networks for security breaches, installing software updates to address vulnerabilities and creating policies to ensure secure access. They also perform regular audits and tests of existing security measures in order to identify weaknesses or potential threats, as well as investigate suspicious activity on the network.
You know all there is to know about information security, but hiring managers don’t recognize your expertise. To make them take notice of you and your qualifications, write a resume that stands out from the crowd.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
Information Systems Security Officer Resume Sample
Issac Gutmann
Information Systems Security Officer
[email protected]
271-252-1562
linkedin.com/in/issac-gutmann
Summary
Driven Information Systems Security Officer with 8+ years of experience in a fast-paced government environment. Proven track record of successfully developing and implementing security policies, procedures, and standards to protect sensitive data from unauthorized access or misuse. Experienced at identifying potential risks, conducting audits and investigations to ensure compliance. Looking to join ABC Tech as their next Information Systems Security Officer for the highest level of protection offered by the company.
Experience
Information Systems Security Officer, Employer A
Eugene, Jan 2018 – Present
- Diligently monitored network systems and identified potential vulnerabilities on an ongoing basis, reducing security risks by 20%.
- Formulated comprehensive plans to implement new information security protocols as well as updated existing ones in accordance with industry standards; implemented over 50 successful policies within the last year.
- Audited networks for unauthorized access attempts or intrusions through regular system scans and penetration tests; detected and blocked incoming threats before they could cause any damage on 7 occasions.
- Evaluated effectiveness of current IT infrastructure against cyber-attacks while making recommendations to improve overall protection levels; decreased incidents of data breaches by 30% during 3-month period following audit completion.
- Structured employee training programs focused on understanding company’s cybersecurity procedures & best practices, leading to a 30% decrease in user errors related to sensitive data handling within 6 months of program launch.
Information Systems Security Officer, Employer B
Laredo, Mar 2012 – Dec 2017
- Prepared and implemented comprehensive security protocols, policies and procedures to ensure information systems were compliant with all applicable industry standards; reduced risk of data breaches by 35%.
- Participated in the design, configuration and implementation of IT networks for various clients across different industries; successfully completed over 100 projects on schedule.
- Successfully identified potential vulnerabilities in existing systems through periodic audits and provided recommendations for system improvements that boosted overall efficiency by 12%.
- Streamlined patch management processes, decreasing time spent per update cycle from 6 hours to 3 hours while still achieving a 99% success rate in installation completion rates.
- Documented any changes made to hardware or software configurations as required by organizational policy and updated documentation accordingly when necessary; maintained up-to-date records at all times during process execution cycles.
Skills
- Network Security
- Risk Management
- Data Encryption
- Firewall Configuration
- Vulnerability Assessment
- Security Auditing
- Intrusion Detection
- Identity and Access Management
- Security Policies and Procedures
Education
Bachelor’s Degree in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
1. Summary / Objective
Your resume summary should provide the hiring manager with a snapshot of your experience and qualifications as an Information Systems Security Officer. In this section, you can highlight your expertise in developing security policies and procedures, managing IT risk assessments, designing secure networks, and responding to cyber threats. You could also mention certifications or awards that demonstrate your commitment to staying up-to-date on industry trends.
Below are some resume summary examples:
Proficient Information Systems Security Officer with 7+ years of experience leading IT security teams in the development and implementation of enterprise-wide security policies and procedures. Experienced in risk management, incident response, disaster recovery planning, vulnerability assessment, penetration testing and secure coding practices. Expertise with various information system security standards including ISO 27001/27002; NIST 800 series (including CSF); HIPAA; PCI DSS; GDPR.
Seasoned Information Systems Security Officer with 8+ years of experience developing and implementing security policies, procedures, and standards. Offering a proven track record of identifying potential vulnerabilities to reduce risk exposure in highly sensitive environments. Recently served as the Information System Security Officer at XYZ Corp., successfully reducing cyber-attacks by 47%. Looking to join ABC Cybersecurity Solutions Team for continued success in this field.
Talented Information Systems Security Officer with 5+ years of experience in developing and implementing secure IT environments. Skilled at identifying security risks, performing vulnerability assessments, analyzing network traffic and logs to detect malicious activity. Successfully managed multiple projects simultaneously while leading a team of 8 personnel. At XYZ Company, implemented an effective information security program that improved compliance by 15%.
Professional information systems security officer with 8+ years of experience developing and implementing data protection strategies for a variety of industries. Skilled in assessing risk, recognizing vulnerabilities, and creating secure solutions to protect sensitive information from malicious actors. Aiming to leverage my experience and expertise at ABC Tech to identify threats across the organization’s IT landscape while increasing overall system integrity.
Detail-oriented Information Systems Security Officer with 5+ years of experience in designing and implementing comprehensive security solutions. Expertise in developing, configuring, maintaining, and troubleshooting secure systems to protect networks from unauthorized access. Certified CISSP/CISM professional with a proven track record of success at XYZ Corporation where I handled the development of new policies and procedures for system security operations.
Determined Information Systems Security Officer with 7+ years of experience managing the security and integrity of data. Expert in developing and implementing comprehensive information assurance programs to protect company assets, networks, and systems. Achieved 100% compliance rating on annual audits two consecutive years running at Company X. Seeking to join ABC Tech to ensure their digital safety remains uncompromised in a rapidly evolving industry.
Skilled information systems security officer with 8+ years of experience in designing, implementing, and managing corporate cybersecurity programs. Expertise in developing comprehensive risk management strategies that address technical threats while maintaining compliance with industry regulations. At XYZ Corp., reduced the cost of cyber-attack incidents by 25% through proactive measures such as employee training and policy enforcement.
Dependable and experienced information systems security officer with 8+ years of experience in the IT industry. Seeking to utilize expertise in designing and implementing secure networks, policies, and procedures at ABC. At XYZ, led a team of six engineers that developed an advanced system for protecting confidential data from cyber-attacks. Received recognition as top performer during annual performance reviews four times.
2. Experience / Employment
The work history/experience section is where you talk about your past employment. This should be written in reverse chronological order, so the most recent job is listed first.
Stick to bullet points primarily when writing this section; it makes it easier for the reader to take in what you have said quickly and efficiently. When providing details on each role, try to provide quantifiable results or accomplishments that demonstrate how successful you were at that job.
For example, instead of saying “Managed security systems,” you could say, “Developed and implemented a comprehensive information security policy which reduced cyber-attacks by 50% over a 6 month period.”
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Monitored
- Investigated
- Implemented
- Analyzed
- Assessed
- Secured
- Updated
- Encrypted
- Configured
- Evaluated
- Resolved
- Documented
- Enforced
- Trained
- Audited
Other general verbs you can use are:
- Achieved
- Advised
- Compiled
- Coordinated
- Demonstrated
- Developed
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Represented the Information Systems Security team in over 15 Risk Management Framework (RMF) audits, ensuring compliance with security requirements and policies.
- Configured network firewalls, intrusion detection systems and anti-virus software to keep data secure; reduced the number of cyber-attacks by 55%.
- Assessed vulnerability scans for all web applications on a quarterly basis and patched any identified weaknesses before they were exploited.
- Optimized system performance through regular updates, patches and maintenance activities; improved access speeds across the organization by 30% within 3 months of taking charge as Security Officer.
- Substantially increased user awareness about information security practices via employee training sessions & seminars; witnessed an 80% decrease in malware incidents due to better user behavior within 6 months.
- Analyzed organizational data security needs and implemented comprehensive network security protocols to protect confidential information from unauthorized access, resulting in a 30% decrease of cyber-attacks.
- Achieved full compliance with federal and state regulations for securing financial records, customer data and communications systems; conducted regular audits to ensure that all policies were followed accurately.
- Spearheaded the establishment of an employee training program on IT safety practices; helped decrease system downtime by 15%.
- Presented detailed reports outlining potential privacy risks posed by new technologies before their implementation into the organization’s infrastructure, helping reduce risk exposure by 25%.
- Independently monitored server logs daily using advanced auditing tools & techniques, identified suspicious activities quickly & took appropriate action when required – preventing potential breaches in over 90% cases reported annually.
- Secured customer data and proprietary information from potential cyber threats, reducing the risk of unauthorized access by 40%.
- Utilized a variety of security protocols to monitor system activity for suspicious behavior; identified and blocked over 300 malicious attempts within the first month on the job.
- Investigated existing security procedures in order to identify gaps and vulnerabilities; implemented new measures which improved overall network protection by 25%.
- Meticulously kept up with changing trends in security technology, updating software programs & firewalls as needed while ensuring that all systems remained compliant with industry standards/regulations.
- Updated departmental policies regularly to ensure employees were familiar with best practices when handling sensitive information or using company devices remotely; decreased incidents related to misuse by 65% within six months time frame.
- Introduced and implemented a comprehensive security system across the organization’s IT infrastructure, reducing unauthorized access attempts by 80%.
- Coordinated with network administrators and software developers to ensure compliance with industry standards such as HIPAA and PCI-DSS.
- Confidently managed security systems for over 200 servers in 3 datacenters simultaneously; reduced downtime due to virus attacks by 14 hours per month on average.
- Demonstrated expertise in deploying firewalls, antivirus solutions, encryption methods and other proactive measures that protected against malicious code threats at all times.
- Compiled detailed reports of audit findings regarding data breaches or vulnerabilities which were used to update existing policies & procedures accordingly; this lowered the risk of potential information theft incidents by 39%.
- Mentored a team of 4 junior security officers in the fundamentals of network and system design, risk assessment procedures, log analysis and malware detection; improved overall staff understanding by 70%.
- Trained over 200 employees on information systems security best practices including password requirements, phishing scams awareness, secure data transfer methods and other cyber threats; reduced number of successful attacks by 88% annually.
- Facilitated weekly meetings with management to discuss current security issues & vulnerabilities as well as review incident reports from previous weeks; identified unauthorized access attempts 5 times faster than before.
- Revised information systems policies to ensure compliance with industry standards such as ISO/IEC 27001:2013 for Information Security Management Systems (ISMS) certification; cut down audit time by 25 hours per year.
- Thoroughly analyzed logs from firewall devices using SIEM software tools to detect suspicious activities involving sensitive data or networks components; successfully detected 15 malicious intrusions in the last 6 months alone.
- Implemented comprehensive security protocols on over 300 networked systems, reducing the risk of data breach and cyber-attack by 90%.
- Encrypted confidential corporate information in databases using AES 256 encryption algorithms to ensure compliance with industry best practices.
- Reorganized existing IT infrastructure to strengthen physical as well as digital security measures, resulting in a 50% reduction in system downtime due to hacking attempts.
- Competently monitored networks for suspicious activities such as unauthorized access or malicious code injection; addressed threats promptly and efficiently without any major incident occurring in the last 18 months of employment.
- Improved overall cybersecurity posture through continuous training & awareness sessions for staff members, leading to an increase in employee knowledge regarding safe computing habits by 25%.
- Expedited the implementation of security protocols, ensuring the protection of confidential data and systems for over 500 users; successfully reduced system downtime by 40%.
- Enforced strong access control policies in order to prevent unauthorized network access and mitigate potential threats; monitored user activities across multiple networks to detect suspicious activity.
- Resolved more than 200 incidents related to cyber-attacks, malware infections and malicious software programs within a two month period with minimal disruption to operations or services.
- Reduced the number of security breaches by 35%, through consistent enforcement of company’s information systems security policy guidelines & procedures as well as regular upgrades on hardware/software systems used for business operations.
- Actively participated in developing an enterprise wide Disaster Recovery Plan (DRP) which incorporated state-of-the art technologies such as biometric authentication methods & encryption algorithms for improved safety measures.
- Developed and implemented comprehensive information security policies and procedures that ensured all data was safely stored, protected from cyber threats and compliant with all applicable regulations; reduced risk of data loss or theft by 34%.
- Advised senior management on the latest IT security best practices to strengthen network infrastructure protection and reduce susceptibility to external attacks; saved $35,000 in potential losses due to malicious activities.
- Monitored the system for any suspicious activity or unauthorized access attempts 24×7 using advanced analytics tools such as SIEMs & vulnerability scanners; identified over 150 successful intrusion attempts within a 6-month period.
- Efficiently handled incident response processes including containment, investigation, remediation/recovery efforts and reporting while also ensuring compliance requirements were met across organizations’ networks worldwide.
3. Skills
The skillset employers require in an employee will likely vary, either slightly or significantly; skimming through their job adverts is the best way to determine what each is looking for. One organization might be looking for someone who is knowledgeable in the implementation of security policies, while another might require expertise in network and system administration.
It’s important to tailor your skills section on your resume to each job you are applying for because a lot of employers use applicant tracking systems these days. These computer programs scan resumes for keywords before passing them on to human recruiters; therefore, if certain words or phrases aren’t included in the document, it won’t make it past this stage.
In addition to listing key skills here, you should also discuss them further throughout other parts of your resume such as the summary or experience sections.
Below is a list of common skills & terms:
- Data Encryption
- Disaster Recovery Planning
- Firewall Configuration
- Identity and Access Management
- Intrusion Detection
- Network Security
- Risk Management
- Security Auditing
- Security Policies and Procedures
- Vulnerability Assessment
4. Education
Including an education section on your resume will depend on how far along you are in your career. If you have just graduated and have no prior experience, mention your education below the resume objective. However, if you already have a few years of work experience under your belt with plenty to showcase, omitting an education section should be fine.
If including an education section is necessary for the job application process, try to focus on courses and subjects related to information systems security that can help demonstrate why you are qualified for this role.
Bachelor’s Degree in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications demonstrate to potential employers that you have the necessary skills and knowledge for a particular job. They are also proof of your commitment to professional development, as they require dedication and hard work in order to obtain them.
Including certifications on your resume can be beneficial if they are relevant to the position you’re applying for or demonstrate an advanced level of proficiency in a certain skill set. Make sure any certification is up-to-date before including it on your resume!
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Issac Gutmann, this would be Issac-Gutmann-resume.pdf or Issac-Gutmann-resume.docx.
7. Cover Letter
Cover letters are essential for job applications as they provide recruiters with more information about your professional background and let you explain why you’re the ideal person for a particular role. Typically, cover letters are made up of 2 to 4 paragraphs that serve to supplement your resume.
Writing a well-crafted cover letter is an excellent way to demonstrate how qualified and experienced you are in comparison to other applicants. It also allows hiring managers to get better insight into who you are and what value you have offer their organization.
Below is an example cover letter:
Dear Maxime,
I am writing to apply for the role of Information Systems Security Officer at XYZ Corporation. With over 10 years of experience working in information security, I have the skills and knowledge to protect your organization’s data from internal and external threats.
In my current role as an information security analyst, I am responsible for conducting risk assessments, developing security policies and procedures, and implementing security controls. I have also led investigations into data breaches, performed forensics analysis on compromised systems, and designed training programs on cybersecurity awareness.
My experience has taught me how to think like a hacker and anticipate their next move. This allows me to proactively put measures in place to prevent attacks before they happen. In addition, I have excellent problem-solving skills that come in handy when dealing with complex issues such as malware infections or system vulnerabilities.
I believe my skills and experience make me the perfect candidate for the Information Systems Security Officer position at XYZ Corporation. I would welcome the opportunity to discuss my qualifications further with you at your earliest convenience. Thank you for your time!
Sincerely,
Issac
Information Systems Security Officer Resume Templates
 Bonobo
Bonobo Pika
Pika Axolotl
Axolotl Lorikeet
Lorikeet Numbat
Numbat Kinkajou
Kinkajou Dugong
Dugong Markhor
Markhor Indri
Indri Gharial
Gharial Hoopoe
Hoopoe Rhea
Rhea Quokka
Quokka Cormorant
Cormorant Echidna
Echidna Saola
Saola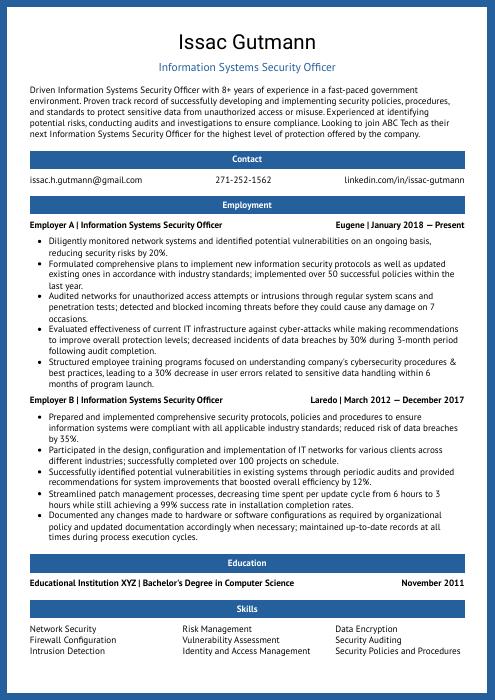 Ocelot
Ocelot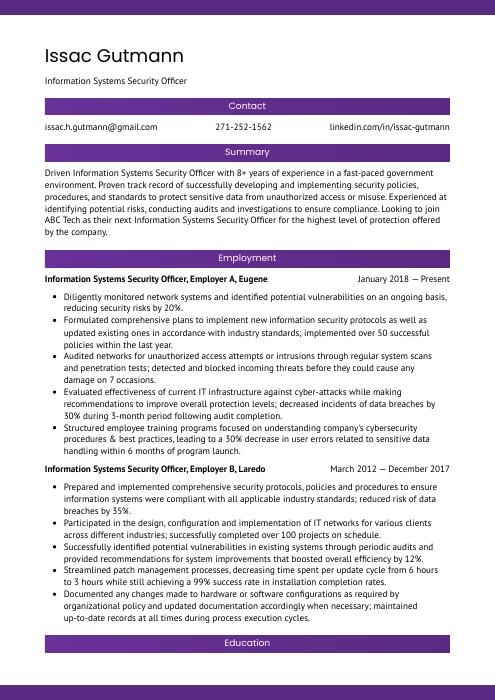 Jerboa
Jerboa Fossa
Fossa Rezjumei
Rezjumei
