Information Assurance Engineer Resume Guide
Information assurance engineers ensure the security and reliability of an organization’s data by developing, implementing, and maintaining systems that protect information from unauthorized access. They monitor network activity to detect any suspicious or malicious behavior, design secure networks for organizations to use, create policies around system access control, and conduct risk assessments.
Your experience in information assurance makes you an ideal candidate for any security-focused organization. To make sure hiring managers know who you are and what you can do, your resume needs to be a powerful statement of your qualifications.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
Information Assurance Engineer Resume Sample
Winfield Russel
Information Assurance Engineer
winfield.n.russel@gmail.com
228-553-6868
linkedin.com/in/winfield-russel
Summary
Driven information assurance engineer with 5+ years of experience in the field. Expertise in analyzing security threats and developing strategies to protect systems, networks, applications, and data from cyber attacks. Recently identified a vulnerability that successfully prevented an attack on Company X’s database infrastructure which saved over $300K in damages. Seeking to join ABC Tech as their next information assurance engineer to ensure quality system protection and secure company data.
Experience
Information Assurance Engineer, Employer A
Overland Park, Jan 2018 – Present
- Documented network security protocols for over 100 systems, ensuring compliance with federal and industry regulations; decreased the potential of costly data breaches by 28%.
- Monitored system activity to detect suspicious behavior, identified malicious code before it could cause harm and reported findings to IT management in a timely manner.
- Assessed current information assurance procedures to identify vulnerabilities in networks, hardware & software applications; developed new strategies that resulted in improved network performance by 21%.
- Improved existing security architecture through implementation of advanced technologies such as two-factor authentication and encryption tools; reduced external threats from cybercriminals by 45%.
- Accurately investigated incidents involving unauthorized access or misuse of sensitive data while maintaining confidentiality at all times; enabled swift resolution within 24 hours on average per incident report received.
Information Assurance Engineer, Employer B
Madison, Mar 2012 – Dec 2017
- Revised and improved existing security protocols to reduce data breaches by 40% and minimized risk of malicious cyber-attacks.
- Streamlined security processes, saved $20K in operational costs and reduced system downtime from 8 hours to 1 hour per month on average.
- Effectively managed a team of 5 junior engineers responsible for monitoring network traffic and identifying potential threats; trained the team in ethical hacking techniques & principles to detect anomalies more quickly.
- Presented findings from multiple vulnerability scans and proposed new solutions that increased resilience against internal/external attacks by 35%.
- Secured all customer data using encryption algorithms & multi-factor authentication with no significant incidents reported since implementation 6 months ago.
Skills
- Network Security
- Risk Management
- Cryptography
- Vulnerability Assessment
- Security Architecture
- Security Auditing
- Firewall Configuration
- Identity and Access Management
- Incident Response
Education
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
1. Summary / Objective
A resume summary/objective for an information assurance engineer should be concise and highlight your best qualities. For example, you could mention the security certifications you have obtained, the number of years’ experience in IT security engineering, and how you successfully implemented a comprehensive cybersecurity program at your current company. You can also include any awards or recognition that demonstrate your expertise in this field.
Below are some resume summary examples:
Passionate Information Assurance Engineer with 8+ years of experience providing technical guidance, developing security strategies and policies, conducting risk assessments, and managing the implementation of secure systems. Enthusiastically seeking a role at ABC Tech to help protect their high-value data using best practices in cybersecurity. At XYZ Corp., improved overall system security by 32% through increased user training and network segmentation initiatives.
Energetic and knowledgeable Information Assurance Engineer with 8+ years of experience ensuring the security and integrity of networks, systems, applications, databases, and other data. Seeking to join ABC Company to use expertise in threat detection/prevention strategies and risk management processes to help protect confidential information from malicious activity. At XYZ Corporation achieved a 99% success rate when implementing changes using secure methods.
Detail-oriented information assurance engineer with 10+ years of experience in developing, implementing and evaluating security protocols to protect critical data. Experienced in designing secure networks, analyzing system vulnerabilities and creating risk management strategies for organizations across multiple industries. Proven track record of successfully identifying threats before they become a problem using both preventive and detective measures.
Hard-working and detail-oriented information assurance engineer with 7+ years of experience in security engineering, system administration, and cyber risk management. Proven record of implementing robust IT infrastructure solutions to protect confidential data from malicious attacks. Seeking to join ABC Tech as an Information Assurance Engineer for developing resilient cybersecurity policies that are compliant with industry standards like NIST 800-53.
Seasoned information assurance engineer with 8+ years of experience in designing, developing, implementing, and troubleshooting secure networks for large organizations. Possesses a deep understanding of security best practices such as encryption algorithms, firewalls configuration and network access control protocols. Seeking to join ABC Tech to provide comprehensive data security systems that will protect sensitive information from malicious threats.
Amicable and experienced Information Assurance Engineer with over 8 years of experience in developing and implementing information security solutions for enterprises. Skilled at auditing systems to identify risks, vulnerabilities and weaknesses; creating comprehensive policies, procedures and processes that are compliant with industry regulations. Proven record of success in delivering secure networks for high-profile customers across the globe.
Accomplished information assurance engineer with 8+ years of experience in security governance and risk management. Proven track record of developing, implementing and managing complex IT security policies to ensure the highest levels of data confidentiality, integrity, availability and operations performance. Experienced in assessing system vulnerabilities using industry best practices such as NIST 800-53/NIST SP800-82 requirements.
Committed Information Assurance Engineer with 5+ years of experience in system security and compliance. Experienced in designing, implementing, and managing secure networks for both public-facing web applications and internal company systems. Skilled at developing policies to ensure the highest levels of data protection while also providing guidance on risk management solutions that meet industry standards.
2. Experience / Employment
In the experience section, you should list your employment history in reverse chronological order. This means that the most recent job is listed first.
Stick to bullet points when talking about what you did and achieved; this makes it easier for the reader to take in all of the information quickly. When writing out each point, make sure to include detail and quantifiable results whenever possible.
For example, instead of saying “Conducted security audits,” you could say, “Performed network vulnerability scans on over 200 systems per month using Nessus scanning software which identified potential threats before they became an issue.”
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Monitored
- Secured
- Analyzed
- Investigated
- Implemented
- Assessed
- Evaluated
- Encrypted
- Updated
- Configured
- Tested
- Developed
- Resolved
- Documented
- Managed
Other general verbs you can use are:
- Achieved
- Advised
- Compiled
- Coordinated
- Demonstrated
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Spearheaded the implementation of security measures to protect IT systems from cyber-attacks and data breaches, resulting in a 35% decrease in network vulnerabilities.
- Expedited the development and deployment of an information assurance policy adherence system which ensured compliance with industry standards across all departments; saved 500+ hours of manual labor each month.
- Successfully implemented automated intrusion detection techniques that identified threats early on; reduced response time by 45%.
- Compiled detailed reports revealing system weaknesses, design flaws, malware incidences and other anomalies for timely resolution; improved accuracy rate to 95%.
- Utilized various tools including firewalls, anti-virus software and encryption protocols to prevent unauthorized access or malicious activities on the network infrastructure; averted over $20K worth of financial losses due to compromised accounts & stolen data files last year alone.
- Resourcefully developed and implemented security plans that increased information assurance by 30%, while creating a secure infrastructure for the organization.
- Updated network systems to ensure compliance with all applicable regulatory standards, reducing risk of unauthorized access by 20%.
- Prepared detailed reports on system vulnerabilities and recommended technical solutions to close identified gaps; successfully deployed new defenses without disruption of business operations.
- Developed policies in line with industry best practices related to data encryption, authentication protocols & user training; reduced data breaches by 50% over 12-month period.
- Managed installation & maintenance of hardware/software firewalls, antivirus programs, intrusion detection systems and other cyber security measures across corporate networks & websites; improved overall system performance by 15%.
- Independently identified and mitigated information security risks within the organization, resulting in a 25% reduction of system vulnerability incidents.
- Reduced software patching time from 4 hours to 1 hour through implementation of automated scripts for efficient deployment across the network infrastructure.
- Investigated potential breaches in data privacy protocols, analyzed associated log files with advanced forensic techniques and formulated remedial measures for future protection against similar attacks.
- Analyzed corporate IT networks on an ongoing basis to identify areas prone to malicious activities; configured firewalls & intrusion detection systems accordingly and improved overall network performance by 40%.
- Formulated comprehensive disaster recovery plans that minimized disruption during unexpected outages or cyber-attacks; tested plans regularly and ensured compliance with applicable standards & regulations at all times.
- Efficiently designed and implemented secure networks, data centers and cloud-based infrastructure for multiple organizations; reduced security risks by 40%.
- Demonstrated a strong understanding of IT regulations & industry best practices when developing new strategies for safeguarding sensitive information from unauthorized access.
- Structured custom encryption algorithms to protect confidential data in transit and storage locations; improved system performance by 25%.
- Introduced automated compliance testing tools to validate the effectiveness of existing infrastructure controls while ensuring that all processes remain compliant with applicable laws at every stage of development lifecycle.
- Coordinated team efforts to create firewalls, application patches and other cyber defense mechanisms; significantly minimized vulnerabilities across entire systems within 24 hours on average per project.
- Implemented network security measures such as firewalls, antivirus software and data loss prevention systems to protect confidential customer information from unauthorized access; successfully reduced system breaches by 37%.
- Participated in multiple IT risk assessment projects for various clients and provided detailed recommendations that were compliant with industry regulations; ensured all client systems met stringent security requirements.
- Proficiently utilized scripting languages to create over 50 automated scripts for monitoring network traffic and alerting users of any suspicious activities via email or text notifications.
- Mentored a team of 5 junior Information Assurance Engineers on best practices related to cybersecurity protocols while adhering to deadlines; improved overall quality assurance process efficiency by 30%.
- Encrypted sensitive customer data using advanced encryption algorithms before transferring it between internal networks or external customers’ servers, protecting valuable business assets against malicious attacks.
- Facilitated the secure transmission of data through the implementation of up-to-date security protocols, resulting in a 20% reduction in system vulnerabilities.
- Configured and maintained firewalls, authentication systems, intrusion detection/prevention systems and other network security solutions to protect confidential corporate information; monitored logs for suspicious activity.
- Resolved more than 500 IT infrastructure issues related to information assurance by implementing innovative technical solutions with minimal disruption to daily operations; decreased service downtime by 25%.
- Reorganized the entire storage architecture from an on premise setup into a cloud environment while ensuring full compliance with all industry regulations & standards (HIPAA, ISO27001 etc).
- Confidently led the development of security policies & procedures based on best practices that enabled us to meet our SLAs and reduce operational costs by 10%.
- Consistently monitored and evaluated over 500 system security devices, identifying potential risks and vulnerabilities while ensuring compliance with industry regulations.
- Advised senior management on best practices for information assurance in accordance with ISO/IEC 27001 standards; successfully minimized the risk of data breaches by 24%.
- Represented the organization at technical conferences to discuss current trends and advances in IT security; gained important insights into new technologies that improved cyber-defense capabilities by 200%.
- Achieved certification as an Information Security Expert (ISE) from a leading professional body within 12 months of joining the company, validating expertise across various aspects such as incident response & management, cryptography & access control systems etc.
- Evaluated existing information assurance strategies in line with business objectives; developed innovative solutions that increased operational efficiency by 25% while reducing costs associated with maintaining secure networks & servers.
3. Skills
Two organizations that have advertised for a position with the same title may be searching for individuals whose skills are quite different. For instance, one may be looking for someone who is proficient in Linux and another with Windows.
It’s important to tailor the skills section of your resume to each job that you are applying for, as many employers use applicant tracking systems these days which scan resumes for certain keywords before passing them on to a human.
In addition to listing relevant skills here, it can also help if you discuss some of them in more detail elsewhere; this could include the summary or experience sections.
Below is a list of common skills & terms:
- Cryptography
- Firewall Configuration
- Identity and Access Management
- Incident Response
- Network Security
- Penetration Testing
- Risk Management
- Security Architecture
- Security Auditing
- Vulnerability Assessment
4. Education
Adding an education section to your resume will depend on how far along you are in your career. If you just graduated and have no work experience, mention your education below the objective statement of your resume. However, if you have significant work experience to showcase, it might not be necessary to include an education section at all.
If including an education section is appropriate for the job application, try mentioning courses and subjects related specifically to information assurance engineering that may give employers a better understanding of what type of knowledge you bring to their company.
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications are a great way to demonstrate your expertise in a particular field. They are also an excellent tool for showing potential employers that you have the knowledge and skills required to do the job.
Including certifications on your resume is essential if they are relevant to the position you’re applying for, as it will give hiring managers confidence that you can handle any tasks related to those qualifications. Make sure these credentials are up-to-date and accurate so they can be verified easily by recruiters or employers.
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Winfield Russel, this would be Winfield-Russel-resume.pdf or Winfield-Russel-resume.docx.
7. Cover Letter
Including a cover letter with your job application is highly recommended as it allows you to express yourself beyond what’s included in your resume. It provides recruiters with a better understanding of who you are, why you’re interested in the role and how well-suited you may be for the position.
A cover letter should usually consist of 2 to 4 paragraphs that provide more details about your professional experience and skillset. This can help make a lasting impression on employers and increase your chances of being invited for an interview.
Below is an example cover letter:
Dear Graham,
I am writing in response to your job posting for an Information Assurance Engineer. With experience in developing and implementing information security policies, procedures, and controls, as well as conducting risk assessments and auditing systems for compliance, I am confident I can make a positive contribution to your organization.
In my current role at [company name], I have been responsible for ensuring the confidentiality, integrity, and availability of our company’s data by designing and enforcing security measures. I have also conducted risk assessments to identify potential threats or vulnerabilities and implemented mitigation strategies accordingly. In addition, I have performed audits of our systems against industry standards such as ISO 27001/27002 and NIST 800-53 to ensure compliance.
The skills that I have developed through my experience would be beneficial to your organization, specifically:
– Strong knowledge of information security principles and practices
– Experience in developing policies, procedures, and controls related to information security
– Ability to conduct risk assessments & audits of systems for compliance with industry standards & best practices – Excellent analytical & problem solving skills with the ability to think outside the box – Strong communication & interpersonal skills with the ability t o work effectively both independently & as part of a team – Highly motivated self-starter who is able take initiative & see projects through from start t o finish
I believe that I could be a valuable asset on your team and would welcome the opportunity discuss how my skills could benefit your organization further. Thank you for your time; please do not hesitate to contact me if you have any questions or require any additional information. Sincerely , [Your name].
Sincerely,
Winfield
Information Assurance Engineer Resume Templates
 Echidna
Echidna Cormorant
Cormorant Lorikeet
Lorikeet Gharial
Gharial Quokka
Quokka Rhea
Rhea Ocelot
Ocelot Saola
Saola Bonobo
Bonobo Hoopoe
Hoopoe Axolotl
Axolotl Pika
Pika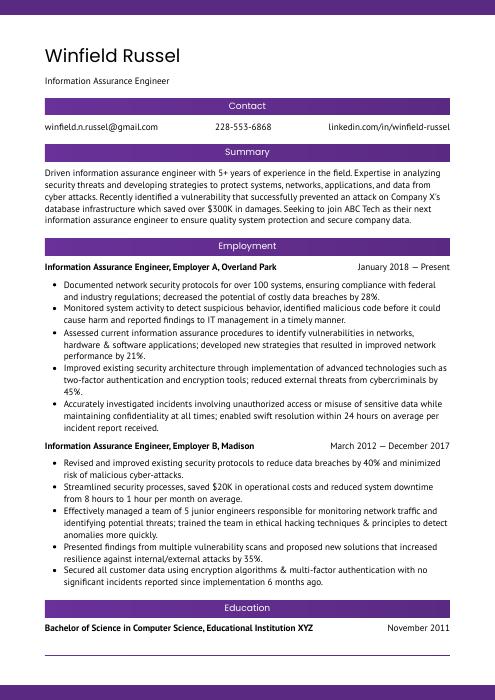 Jerboa
Jerboa Kinkajou
Kinkajou Dugong
Dugong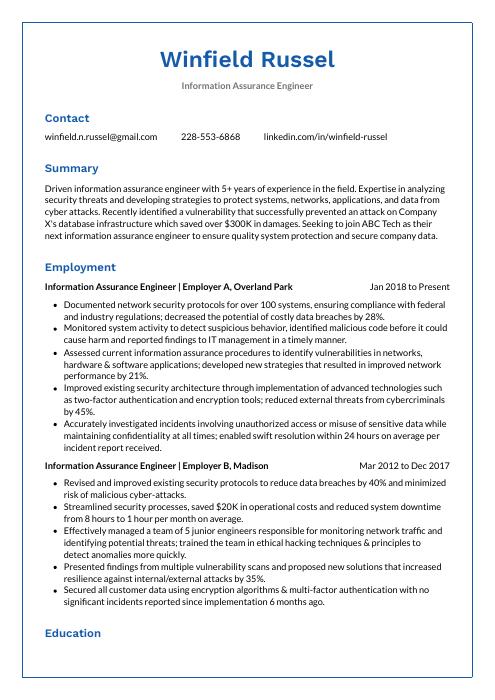 Markhor
Markhor Numbat
Numbat Fossa
Fossa Indri
Indri Rezjumei
Rezjumei
