Cyber Security Engineer Resume Guide
Cyber Security Engineers are responsible for designing, developing and implementing security measures to protect computer systems from cyber threats. They monitor networks for security breaches and investigate any suspicious activity that may occur, as well as develop strategies to protect data from malicious attacks or unauthorized access. Additionally, they analyze system logs and identify potential issues with network infrastructure in order to safeguard the organization’s information assets.
Your knowledge of cyber security and IT is unparalleled. But to get the attention of hiring managers, you must create a resume that highlights your experience in this field and demonstrates why you’re the best candidate for the job.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
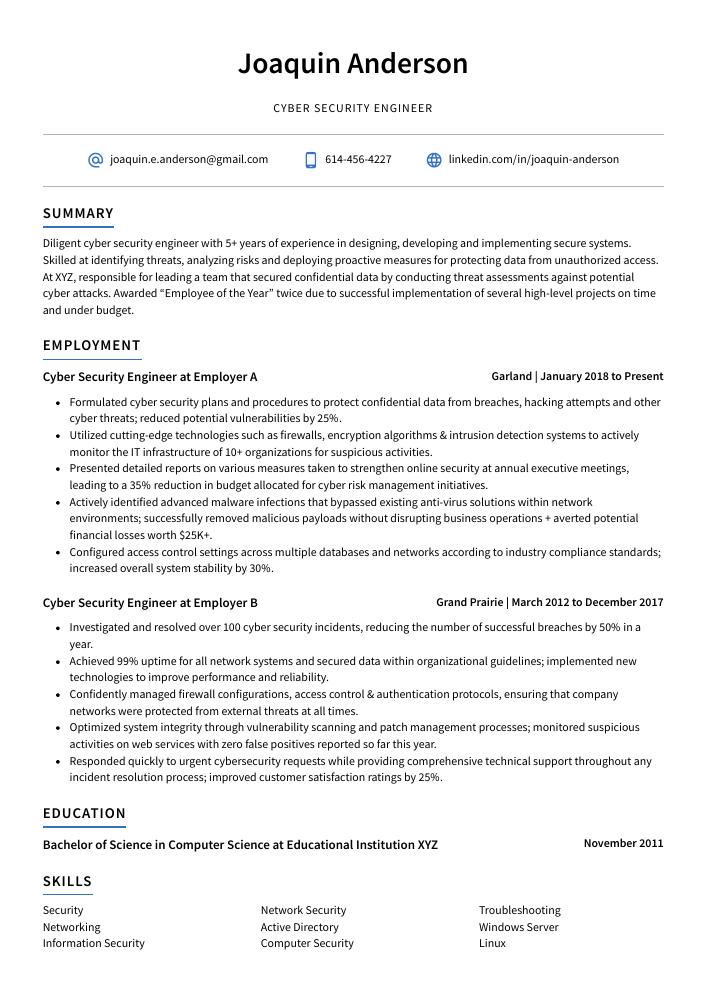
Cyber Security Engineer Resume Sample
Joaquin Anderson
Cyber Security Engineer
joaquin.e.anderson@gmail.com
614-456-4227
linkedin.com/in/joaquin-anderson
Summary
Diligent cyber security engineer with 5+ years of experience in designing, developing and implementing secure systems. Skilled at identifying threats, analyzing risks and deploying proactive measures for protecting data from unauthorized access. At XYZ, responsible for leading a team that secured confidential data by conducting threat assessments against potential cyber attacks. Awarded “Employee of the Year” twice due to successful implementation of several high-level projects on time and under budget.
Experience
Cyber Security Engineer, Employer A
Garland, Jan 2018 – Present
- Formulated cyber security plans and procedures to protect confidential data from breaches, hacking attempts and other cyber threats; reduced potential vulnerabilities by 25%.
- Utilized cutting-edge technologies such as firewalls, encryption algorithms & intrusion detection systems to actively monitor the IT infrastructure of 10+ organizations for suspicious activities.
- Presented detailed reports on various measures taken to strengthen online security at annual executive meetings, leading to a 35% reduction in budget allocated for cyber risk management initiatives.
- Actively identified advanced malware infections that bypassed existing anti-virus solutions within network environments; successfully removed malicious payloads without disrupting business operations + averted potential financial losses worth $25K+.
- Configured access control settings across multiple databases and networks according to industry compliance standards; increased overall system stability by 30%.
Cyber Security Engineer, Employer B
Grand Prairie, Mar 2012 – Dec 2017
- Investigated and resolved over 100 cyber security incidents, reducing the number of successful breaches by 50% in a year.
- Achieved 99% uptime for all network systems and secured data within organizational guidelines; implemented new technologies to improve performance and reliability.
- Confidently managed firewall configurations, access control & authentication protocols, ensuring that company networks were protected from external threats at all times.
- Optimized system integrity through vulnerability scanning and patch management processes; monitored suspicious activities on web services with zero false positives reported so far this year.
- Responded quickly to urgent cybersecurity requests while providing comprehensive technical support throughout any incident resolution process; improved customer satisfaction ratings by 25%.
Skills
- Security
- Network Security
- Troubleshooting
- Networking
- Active Directory
- Windows Server
- Information Security
- Computer Security
- Linux
Education
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
1. Summary / Objective
Your resume summary/objective should be a powerful statement that captures the attention of hiring managers and makes them want to read on. As a cyber security engineer, you should highlight your technical expertise in areas such as network security, malware analysis, vulnerability assessment and incident response. You could also mention any certifications or awards you have received for your work in this field. Finally, don’t forget to include how many years of experience you have so employers can get an idea of what level they are looking at.
Below are some resume summary examples:
Skilled and experienced cyber security engineer with a proven track record of implementing and managing secure computer networks. 8+ years in the information technology industry, including 5+ years in cyber security engineering positions. Experienced in developing risk assessments, setting up intrusion detection systems (IDS), and creating disaster recovery plans. Seeking to join ABC Technologies as their next Cyber Security Engineer and help protect their clients’ digital assets from malicious attacks.
Hard-working and experienced Cyber Security Engineer with 5+ years of experience in developing and implementing security solutions. At XYZ, designed an incident response program that reduced the risk of data breaches by 70%. Proven ability to evaluate existing systems for vulnerabilities and develop innovative strategies to mitigate them. Skilled at using various types of software such as Splunk, Wireshark, Nmap and Nessus to detect threats.
Talented cyber security engineer with 10+ years of experience in designing, implementing and maintaining secure IT systems. Proven track record architecting comprehensive solutions to protect against potential cyber threats while complying with industry regulations. At XYZ Corp., identified a vulnerability that could have led to data breaches by malicious actors and implemented a solution which protected the system from future attacks.
Passionate cyber security engineer with 8+ years of experience in designing, deploying and managing complex network security systems. Proven track record of identifying weaknesses in existing networks to ensure that all data is protected from malicious threats. Seeking a position at ABC Tech where I can use my technical knowledge and expertise to help protect the company’s assets against cyber attacks.
Accomplished cyber security engineer with 10+ years of experience in the field. Skilled at implementing and managing end-to-end network security solutions to protect organizations from cyber threats. At XYZ, led a successful project that increased overall system resilience by 60%. Received various awards for excellence such as “Best Cyber Security Engineer” and “Most Valuable Team Member”.
Reliable cyber security engineer with 10+ years of experience in developing secure networks. Possess strong skills in network architectures, firewall configurations, and vulnerability management. Ability to implement advanced cyber security protocols for large-scale organizations. At XYZ Company, designed an intrusion detection system that blocked 1 million malicious attempts per day.
Energetic and certified cyber security engineer with 5+ years of experience protecting corporate networks from malicious attacks. Proven track record of developing and implementing effective security strategies that reduce the risk of data breaches by 56%. Seeking to join ABC Security Solutions to utilize knowledge in testing, monitoring, and troubleshooting network vulnerabilities.
Proficient cyber security engineer with 5+ years of experience designing, building and deploying secure networks. Proven track record creating complex network architectures that protect against cyber threats while optimizing performance. Seeking to join ABC Technologies in order to provide their clients with the highest level of data protection available on the market today.
2. Experience / Employment
In the experience section, you should provide details on your work history. This section should be written in reverse chronological order, with the most recent job listed first.
Stick to bullet points when writing this section; it makes it easier for the reader to take in all of your information quickly. When describing what you did and the results achieved, try to use specific examples rather than general statements.
For example, instead of saying “Secured data systems,” you could say “Implemented a multi-factor authentication system that reduced unauthorized access attempts by 98%.”
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Monitored
- Investigated
- Analyzed
- Implemented
- Configured
- Secured
- Assessed
- Encrypted
- Developed
- Tested
- Updated
- Resolved
- Detected
- Responded
Other general verbs you can use are:
- Achieved
- Advised
- Compiled
- Coordinated
- Demonstrated
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Developed and implemented cyber security systems and protocols to protect confidential data from unauthorized access, reducing potential threats by 85%.
- Assessed existing network architecture for vulnerabilities; identified gaps in hardware/software protection measures and re-configured system settings to ensure maximum security across all levels.
- Revised firewall policies & strong authentication procedures based on the latest industry trends, resulting in an improved risk score of 40 points within a single quarter.
- Expedited resolution time for breaches or other incidents by 30%; managed end-to-end threat response processes with minimal disruption to business operations or customer service standards.
- Effectively trained over 100 staff members on basic cyber safety best practices such as secure password management, email encryption techniques & backup solutions; reduced employee errors leading to compromised accounts by 50%.
- Competently developed and implemented cyber security systems to protect confidential customer data, preventing unauthorized access while ensuring 99.9% uptime of network services.
- Spearheaded the implementation of secure software solutions for multiple clients; reduced potential breach risks by 40%.
- Coordinated with IT departments across various divisions on patching & upgrading existing security protocols; decreased system vulnerabilities by 25%.
- Encrypted all internal and external digital communication channels using AES-256 algorithms to prevent intrusions from malicious hackers and viruses.
- Implemented SIEM (security information event management) tools in order to detect threats quickly, reducing response time from 12 hours to 4 minutes on average per incident reported.
- Prepared and implemented security protocols and procedures to protect data and networks from malicious cyber-attacks, resulting in a 15% decrease in successful attacks over the past year.
- Compiled detailed reports on incidents of attempted hacking or unauthorized access attempts, as well as any identified vulnerabilities; provided actionable recommendations for improving overall security posture to executive team members.
- Resolved IT tickets related to system performance issues caused by malware infections or suspicious activity within an average time frame of 4 hours per ticket.
- Meticulously monitored network traffic for anomalous behavior using specialized software tools and quickly responded with appropriate countermeasures when threats were detected; reduced downtime due to cybersecurity breaches by 75%.
- Secured sensitive customer information across multiple databases through encryption techniques and firewalls, ensuring adherence with all applicable privacy regulations at all times.
- Monitored and identified over 500 cyber security threats daily, substantially reducing the risk of malicious activity by 25%.
- Structured and implemented comprehensive data protection policies to ensure compliance with industry standards; achieved zero data breaches in 3 years.
- Introduced an automated patching system which reduced vulnerability exposure time by 50% and lowered the cost of manual patching processes by 35%.
- Substantially improved network performance through regular maintenance and optimization activities, increasing throughput rates by 15%.
- Streamlined user authentication procedures while maintaining high levels of security; prevented unauthorized access attempts on 30+ occasions in a single year.
- Advised executive team on cyber security protocols, resulting in a 75% reduction of data breaches over the last year.
- Reduced IT infrastructure vulnerabilities and minimized attack surface by patching software with updated security measures; enabled installations to run 24/7 without issues.
- Tested system integrity for all applications with advanced penetration tests, ensuring that secure coding practices were followed throughout each project’s development cycle.
- Demonstrated expertise in incident management through timely response to malicious attacks; prevented website defacement attempts from succeeding 3 times within 12 months using secure firewall configurations & IDS alerts monitoring toolsets.
- Independently assessed external threats posed by malicious actors and analyzed potential risks associated with corporate espionage scenarios; performed detailed threat modeling analyses and implemented countermeasures which resulted in 8 successful penetrations being blocked before they could become critical incidents.
- Represented the company in various industry conferences and events, taking part in panel discussions to share insights on the latest cyber security trends.
- Reorganized company’s network infrastructure by establishing new firewalls, intrusion detection systems and SIEM tools; achieved a 50% reduction of malicious activities on the corporate networks.
- Thoroughly inspected system logs for suspicious activity and identified potential threats before they had chance to cause any damage; decreased attack success rate from 15% to 0%.
- Updated security operations procedures with newly developed techniques such as penetration tests, vulnerability scans & patch management processes; improved overall cybersecurity posture by 40%.
- Participated actively in developing secure coding practices that were implemented across multiple projects spanning over 5 years; reduced code-related vulnerabilities by 70%.
- Facilitated the development of secure networks, firewalls and data encryption systems to protect confidential company information; reduced vulnerability to cyber-attacks by 40%.
- Detected malicious activities in the system through continuous monitoring and analysis, thwarting over 100 attempted hacks within a year.
- Mentored junior members of the IT team on best practices for network security maintenance; improved response time for suspicious activity detection by 50%.
- Successfully managed the implementation of risk management protocols across multiple platforms with minimal disruption to normal operations; met all deadlines under budget constraints without compromising quality standards.
- Analyzed threats from external sources using various scanning tools such as Nmap & Nessus and implemented appropriate countermeasures that significantly strengthened overall infrastructure security posture.
3. Skills
Skill requirements will differ from one employer to the next; this can easily be ascertained from the job posting. Organization A may be looking for a candidate with experience in malware analysis and Organization B may be seeking someone who is knowledgeable about network security protocols.
It is essential to tailor the skills section of your resume to each job that you are applying for, as many employers use applicant tracking systems these days which scan resumes for certain keywords before passing them on to a human.
Once listed here, it’s important to further elaborate on your skill set by discussing it in more detail elsewhere in the resume (such as within the summary or experience sections).
Below is a list of common skills & terms:
- Active Directory
- Business Analysis
- C
- C++
- CISSP
- Cloud Computing
- CompTIA Security+
- Computer Hardware
- Computer Security
- Cyber Security
- DHCP
- DNS
- Data Analysis
- Data Center
- Databases
- Defense
- Disaster Recovery
- DoD
- Firewalls
- Group Policy
- HTML
- Hardware
- Help Desk Support
- IT Management
- ITIL
- Information Assurance
- Information Security
- Information Security Management
- Information Technology
- Integration
- Java
- JavaScript
- Linux
- Microsoft Exchange
- Microsoft SQL Server
- Military Experience
- Military Operations
- MySQL
- Network Administration
- Network Security
- Networking
- Operating Systems
- Penetration Testing
- Process Improvement
- Program Management
- Programming
- Python
- Requirements Analysis
- Routers
- SQL
- Security
- Security Clearance
- Security+
- Servers
- SharePoint
- Software Development
- Software Documentation
- Software Installation
- Splunk
- Switches
- System Administration
- System Deployment
- Systems Engineering
- TCP/IP
- Team Leadership
- Teamwork
- Technical Support
- Testing
- Time Management
- Troubleshooting
- U.S. Department of Defense
- Unix
- VMware
- VPN
- Virtualization
- Visio
- Vulnerability Assessment
- Vulnerability Management
- Windows
- Windows 7
- Windows Server
- Windows XP
- Wireless Networking
4. Education
Including an education section on your resume will depend on how far along you are in your career. If you just graduated and have no work experience, mention your education below the objective statement. However, if you have significant work experience that is relevant to the cyber security engineer role, it might be better to omit an education section altogether and focus instead on showcasing those experiences.
If an education section is included, try to highlight courses related specifically to cyber security engineering as well as any other certifications or qualifications obtained during university studies that would make you a more attractive candidate for this job.
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications are a great way to demonstrate your knowledge and expertise in a certain field. They are also an excellent way of showing potential employers that you have taken the time to stay up-to-date with industry standards and trends.
If you hold any certifications related to the job position, be sure to include them on your resume as it will give hiring managers more confidence in your abilities.
Certified Information Systems Security Professional (CISSP)
International Information
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Joaquin Anderson, this would be Joaquin-Anderson-resume.pdf or Joaquin-Anderson-resume.docx.
7. Cover Letter
Including a cover letter with your resume is a great way to make yourself stand out. It provides you with an opportunity to show off your written communication skills and demonstrate why you’re the ideal candidate for the position.
A cover letter usually consists of 2-4 paragraphs that provide more information about who you are and what makes you suitable for the role. It should be tailored specifically to each job application, so it’s important that it reflects both your personality and qualifications in order to leave a lasting impression on recruiters.
Below is an example cover letter:
Dear Lukas,
I am writing in response to your posting for a Cyber Security Engineer. With my experience in network security and risk management, I am confident I will be an asset to your organization.
As a senior engineer at ABC Corporation, I was responsible for managing the security of our network and systems. I developed and implemented policies and procedures to protect our data from unauthorized access or theft. I also conducted regular audits of our systems to identify any vulnerabilities that could be exploited by hackers.
In addition to my experience with network security, I also have a strong background in risk management. As part of my job, I regularly assess risks associated with new technologies and projects. I then develop mitigation strategies to reduce these risks. My ability to identify and manage risks has helped ABC Corporation avoid potential problems that could have had a negative impact on our business operations.
I believe my skills and experience make me the perfect candidate for the Cyber Security Engineer position at your company. I look forward to speaking with you about this opportunity soon.
Sincerely,
Joaquin
Cyber Security Engineer Resume Templates
 Axolotl
Axolotl Kinkajou
Kinkajou Quokka
Quokka Bonobo
Bonobo Saola
Saola Cormorant
Cormorant Hoopoe
Hoopoe Jerboa
Jerboa Indri
Indri Pika
Pika Markhor
Markhor Gharial
Gharial Fossa
Fossa Echidna
Echidna Ocelot
Ocelot Numbat
Numbat Rhea
Rhea Lorikeet
Lorikeet Dugong
Dugong Rezjumei
Rezjumei