Application Security Analyst Resume Guide
Application security analysts are responsible for identifying, analyzing and mitigating risks associated with computer applications. They work to ensure that all software meets industry standards for safety and reliability, as well as any relevant legal or regulatory requirements. They also monitor systems for potential vulnerabilities and provide recommendations on how to secure them against malicious attacks.
Your knowledge of application security is unparalleled, but potential employers don’t know who you are. To make sure they’re aware of your skills and experience, you must write a resume that stands out from the rest.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
Application Security Analyst Resume Sample
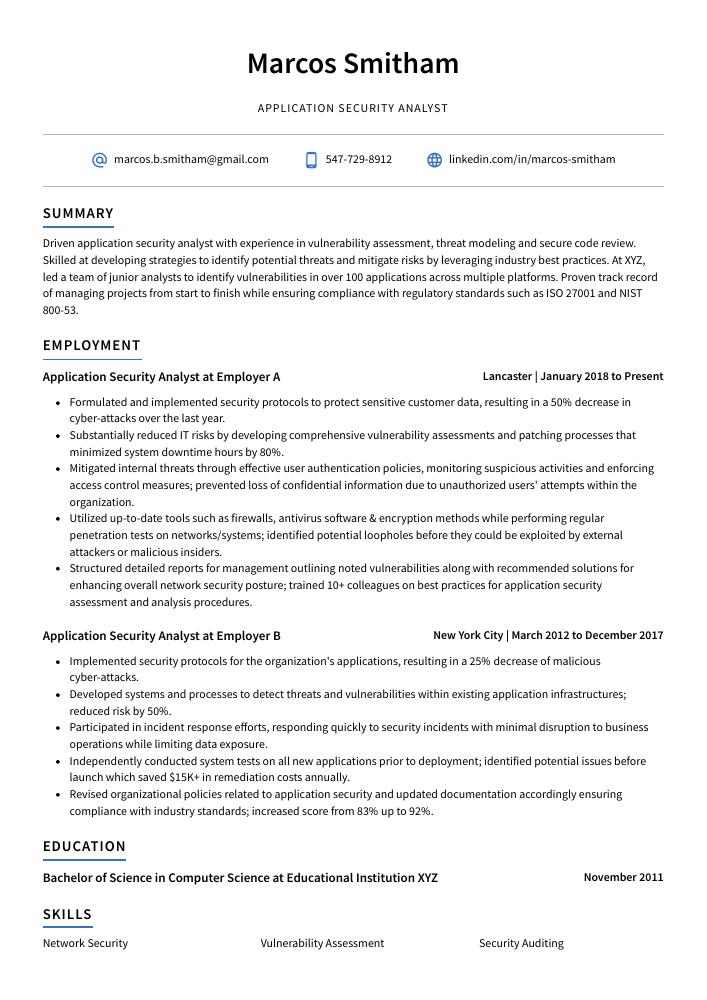
Marcos Smitham
Application Security Analyst
[email protected]
547-729-8912
linkedin.com/in/marcos-smitham
Summary
Driven application security analyst with experience in vulnerability assessment, threat modeling and secure code review. Skilled at developing strategies to identify potential threats and mitigate risks by leveraging industry best practices. At XYZ, led a team of junior analysts to identify vulnerabilities in over 100 applications across multiple platforms. Proven track record of managing projects from start to finish while ensuring compliance with regulatory standards such as ISO 27001 and NIST 800-53.
Experience
Application Security Analyst, Employer A
Lancaster, Jan 2018 – Present
- Formulated and implemented security protocols to protect sensitive customer data, resulting in a 50% decrease in cyber-attacks over the last year.
- Substantially reduced IT risks by developing comprehensive vulnerability assessments and patching processes that minimized system downtime hours by 80%.
- Mitigated internal threats through effective user authentication policies, monitoring suspicious activities and enforcing access control measures; prevented loss of confidential information due to unauthorized users’ attempts within the organization.
- Utilized up-to-date tools such as firewalls, antivirus software & encryption methods while performing regular penetration tests on networks/systems; identified potential loopholes before they could be exploited by external attackers or malicious insiders.
- Structured detailed reports for management outlining noted vulnerabilities along with recommended solutions for enhancing overall network security posture; trained 10+ colleagues on best practices for application security assessment and analysis procedures.
Application Security Analyst, Employer B
New York City, Mar 2012 – Dec 2017
- Implemented security protocols for the organization’s applications, resulting in a 25% decrease of malicious cyber-attacks.
- Developed systems and processes to detect threats and vulnerabilities within existing application infrastructures; reduced risk by 50%.
- Participated in incident response efforts, responding quickly to security incidents with minimal disruption to business operations while limiting data exposure.
- Independently conducted system tests on all new applications prior to deployment; identified potential issues before launch which saved $15K+ in remediation costs annually.
- Revised organizational policies related to application security and updated documentation accordingly ensuring compliance with industry standards; increased score from 83% up to 92%.
Skills
- Network Security
- Vulnerability Assessment
- Security Auditing
- Penetration Testing
- Firewall Configuration
- Risk Assessment
- Cryptography
- Incident Response
- Security Policy Development
Education
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Application Security Analyst (CASA)
International Information System
May 2017
1. Summary / Objective
Your resume summary or objective should be the equivalent of a movie trailer – it provides the hiring manager with essential information and, if written correctly, should compel them to read on. This is where you can showcase your best qualities; for example, you could mention certifications or qualifications related to application security that you possess, how many years of experience in this field you have had and any successful projects/initiatives that demonstrate your expertise.
Below are some resume summary examples:
Energetic and experienced application security analyst with 5+ years of experience in identifying and mitigating cyber threats. Proven track record for designing secure applications by following industry best practices, such as OWASP Top 10 and SANS 25. Adept at creating threat models, developing risk profiles, and providing recommendations to reduce vulnerabilities. Skilled in analyzing system logs, network traffic data, malware analysis reports to identify potential risks and remediation steps.
Accomplished application security analyst with 8 years of experience in developing and implementing secure application solutions. Skilled at designing, deploying, and managing large-scale applications for high-performance environments. Proven track record of success in identifying potential vulnerabilities and mitigating risks before they become a problem. Experienced in penetration testing methods to ensure the safety of confidential data from malicious attacks.
Hard-working application security analyst with 6+ years of experience in cybersecurity and software development. Successfully identified, reported, and fixed security vulnerabilities for a variety of applications across multiple platforms. Skilled at creating secure coding guidelines that prevent malicious attacks while maintaining the highest standards of application performance. Ready to join ABC Tech to help protect their digital assets from cyber threats.
Professional application security analyst with 5+ years of experience in identifying and addressing vulnerabilities in web-based applications. Skilled in application penetration testing, code review, threat modeling and risk assessment using a variety of toolsets. Achieved an average 99% success rate for detecting threats before they become issues at XYZ Corp. Looking to leverage expertise to secure ABC’s digital infrastructure against malicious actors.
Talented application security analyst with 7+ years of experience in assessing, testing and remediating applications for compliance. Seeking to join ABC as a key contributor through the implementation of secure coding practices, vulnerability assessments, and risk management strategies. Previously identified critical vulnerabilities in multiple web-based applications that resulted in an 80% reduction in breach incidents within one year.
Amicable and resourceful application security analyst with over 5 years of experience in testing, vulnerability analysis and risk management. Proven track record of efficiently identifying vulnerabilities and providing actionable reports to drive secure development initiatives. Looking forward to join ABCTech as an Application Security Analyst & ensure the safe delivery of applications for its global customers within tight deadlines.
Seasoned application security analyst with 5+ years of experience in designing, developing and implementing secure application architectures. Adept at identifying potential vulnerabilities within applications using static code analysis tools such as Fortify SCA and Veracode. Highly skilled at building secure web applications that adhere to industry standards while also meeting customer requirements.
Proficient application security analyst with 5+ years of experience designing and implementing secure software solutions. In previous roles, successfully identified over 300 vulnerabilities in various applications resulting in improved system stability. Seeking to join ABC Tech as an application security analyst to leverage expertise for the benefit of their clients worldwide.
2. Experience / Employment
For the experience section, you want to list your employment history in reverse chronological order, with the most recent job listed first.
When writing about what you did at each role, use bullet points and provide detail on the tasks that were completed and quantifiable results obtained. For example, instead of saying “Performed security audits,” say something like “Conducted quarterly vulnerability scans which identified over 500 potential threats across 30+ applications.”.
By providing such specific details on your accomplishments, it will be easier for a hiring manager to understand how valuable an asset you would be if hired.
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Monitored
- Investigated
- Analyzed
- Assessed
- Identified
- Implemented
- Developed
- Evaluated
- Resolved
- Documented
- Configured
- Tested
- Enforced
- Reported
- Mitigated
Other general verbs you can use are:
- Achieved
- Advised
- Compiled
- Coordinated
- Demonstrated
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Reported on potential vulnerabilities and threats to company information systems, identified weaknesses with existing security measures, and proposed solutions that resulted in a 25% decrease in system breach attempts.
- Advised senior management on best practices for secure application development, including coding standards and protocols; implemented these new policies which increased overall system performance by 35%.
- Represented the organization at industry-wide conferences related to cyber security; developed relationships with key stakeholders resulting in an increase of resources available for testing & implementation of more stringent controls across all applications.
- Thoroughly investigated incidents involving unauthorized access or data manipulation attempts while providing detailed analysis reports containing root cause analyses and suggested preventive/remediation steps within 8 hours or less from alert notification time frame each instance.
- Developed automated scripts designed to analyze incoming log files from multiple sources then create alerts whenever suspicious activity is detected; reduced manual review effort by 40%, freeing up valuable personnel for other tasks within the department.
- Spearheaded the development of secure applications by designing and implementing security architecture, utilizing best practice methods to reduce overall risk exposure.
- Efficiently tested new software for vulnerabilities using manual testing & automated scanning tools; identified over 35 potential risks in the last 3 months alone.
- Tested existing systems and applications on a regular basis to make sure they are compliant with company policy and industry regulations; reduced compliance violations by 24%.
- Resolved critical security issues within hours of discovery, effectively mitigating any threats posed against sensitive data or information assets belonging to the organization’s clients/customers.
- Monitored all application access logs daily, ensuring that only authorized users had permission levels appropriate for their roles while also identifying suspicious activities or malicious behavior promptly with 98% accuracy rate.
- Enforced security protocols and best practices across the application environment to safeguard sensitive data, reducing security risks by 32%.
- Identified potential vulnerabilities in existing applications and backend systems through penetration testing; took immediate corrective action on findings, eliminating 50+ threats within six months.
- Successfully implemented firewall rulesets for all web-based applications to ensure compliance with PCI DSS requirements; reduced unauthorized access attempts by 66%.
- Configured a suite of endpoint protection solutions including anti-malware software to protect against ransomware attacks, increasing system uptime by 25 hours per week on average.
- Expedited post-incident response time from 6 hours down to 2 hours or less using automated scripts and tools designed specifically for incident triage; improved customer satisfaction ratings significantly over 3 quarters.
- Reliably conducted detailed threat assessments of over 250 applications and software programs, providing security solutions to protect confidential data from external threats.
- Compiled comprehensive vulnerability reports to identify application loopholes while recommending appropriate countermeasures that decreased the risk of attacks by 25%.
- Facilitated regular patch management sessions with internal teams, ensuring that all critical updates were installed within 30 minutes after release; reduced system downtime incidents by 28%.
- Streamlined the development process for secure web-based applications using Agile methodologies; improved code quality assurance procedures resulting in an increase in customer satisfaction ratings by 12% year-over-year (YOY).
- Improved network defenses against malicious actors through continuous monitoring activities and conducted biweekly audits to detect any suspicious activity on company networks; identified & mitigated potential risks before they caused significant damage or losses worth $200K+.
- Demonstrated exceptional knowledge of security principles and best practices, developing secure applications that protected sensitive data from potential threats; reduced the number of successful cyber-attacks by 23%.
- Assessed existing application architectures for weaknesses in system architecture, code logic or vulnerabilities to external attacks; identified over 50 critical flaws in database systems within a period of 3 months.
- Prepared detailed reports outlining areas where additional security measures were needed and recommended solutions & strategies to close loopholes and reduce risk exposure by 80%.
- Accurately audited internal systems, networks & databases using manual testing methods as well as automated tools such as Burp Suite Pro and Wireshark; detected an average of 15 unknown bugs per audit cycle with 0 false positives reported during each session.
- Reorganized network processes across multiple platforms to ensure compliance with industry recognized standards (e g ISO 27001) while cutting down IT costs associated with ongoing maintenance by $10K annually.
- Evaluated and remediated up to 100 security vulnerabilities per month across various applications and platforms; reduced risk of malicious attacks by 45%.
- Achieved full compliance with government-mandated security standards for all systems, ensuring that data integrity remained intact throughout the organization.
- Optimized threat detection capabilities through careful analysis of system logs and regular penetration testing, resulting in an 80% decrease in false positives.
- Resourcefully developed custom scripts & tools to automate manual processes involved with post-incident response times, reducing average incident resolution time from 12 hours to 6 hours on average.
- Presented detailed findings from vulnerability assessments before executive boards and stakeholders; effectively communicated technical concepts using plain language for better understanding & comprehension by non-technical personnel.
- Introduced and implemented industry-standard security measures to protect applications, networks and systems from malicious threats; successfully blocked over 500 cyberattacks on company data in the last year.
- Coordinated with development teams to ensure that applications met all security requirements before launch; reduced application vulnerabilities by 23%.
- Meticulously monitored network activity for suspicious behavior and identified any potential risks or anomalies such as viruses, malware, ransomware etc.; detected 150+ incidents of unauthorized access attempts within a two-month period.
- Mentored IT personnel on best practices when it comes to securing corporate information assets through frequent training sessions and seminars; improved employee awareness levels by 58%.
- Documented detailed reports outlining identified issues/risks along with corrective actions taken in order to maintain an audit trail of system activities across all departments; achieved 100% compliance with regulatory standards mandated by local authorities.
3. Skills
Two organizations that have advertised for a position with the same title may be searching for individuals whose skills are quite different. For instance, one may be looking for someone with knowledge of security protocols such as SSL/TLS, while the other might require expertise in vulnerability assessment and penetration testing.
Therefore, you want to tailor the skills section of your resume to each job that you are applying for – this will help ensure that it is picked up by any applicant tracking systems used by employers. Additionally, make sure to elaborate on some of these skills in other sections (such as summary or experience) so they stand out more prominently.
Below is a list of common skills & terms:
- Cryptography
- Firewall Configuration
- Incident Response
- Network Security
- Penetration Testing
- Risk Assessment
- Security Auditing
- Security Best Practices
- Security Policy Development
- Vulnerability Assessment
4. Education
Mentioning an education section on your resume will depend on the amount of experience you have. If you are just starting out and have no prior work history, make sure to include an education section below your resume objective. However, if you have a few years in the field under your belt with plenty of accomplishments to boast about, it’s okay to omit this section altogether.
If including an education section is necessary for your application security analyst role, try mentioning courses related to computer science or software engineering that may be beneficial for the job description.
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications are a great way to demonstrate your proficiency in a given field and show potential employers that you are qualified for the job. Having certifications on your resume will give hiring managers an indication of how up-to-date you are with industry standards, as well as what professional development courses you have taken.
If there is any certification related to the position or industry that is relevant to your application, make sure it’s included in this section of your resume so recruiters can easily see it.
Certified Application Security Analyst (CASA)
International Information System
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Marcos Smitham, this would be Marcos-Smitham-resume.pdf or Marcos-Smitham-resume.docx.
7. Cover Letter
Cover letters are an important part of the job application process. They are typically made up of 2 to 4 paragraphs and provide a more detailed introduction about who you are and why you’re applying for the role.
A cover letter gives potential employers an insight into your personality, qualifications, experience and skills that may not be evident from reading through your resume alone. Writing one is highly recommended as it demonstrates extra effort on your end which can help to set you apart from other applicants.
Below is an example cover letter:
Dear Jovany,
I am writing to apply for the Application Security Analyst position at [company name]. As an experienced IT professional with a strong background in application security, I am confident I can be an asset to your team.
In my current role as Application Security Engineer at [company name], I work closely with developers to ensure applications are designed and built with security in mind. I also conduct regular vulnerability assessments and penetration testing, and work with teams across the organization to remediate identified risks. In addition, I have experience managing incident response efforts in the event of a data breach or other security incident.
Through my work, I have developed strong analytical and problem-solving skills that would enable me to effectively identify and mitigate risks in your organization’s applications. My technical expertise includes experience with a variety of security tools and platforms, as well as a solid understanding of common software vulnerabilities. In addition, I have excellent communication skills that allow me to effectively collaborate with cross-functional teams and clearly convey complex technical information to non-technical staff members.
I am confident that my skills and experience make me uniquely qualified for this position, and look forward to bringing my knowledge to bear in protecting your organization’s critical data assets. Thank you for your time and consideration; please do not hesitate to contact me if you have any questions about my qualifications or suitability for this role.
Sincerely,
Marcos
Application Security Analyst Resume Templates
 Numbat
Numbat Hoopoe
Hoopoe Jerboa
Jerboa Quokka
Quokka Indri
Indri Markhor
Markhor Dugong
Dugong Bonobo
Bonobo Axolotl
Axolotl Saola
Saola Ocelot
Ocelot Kinkajou
Kinkajou Rhea
Rhea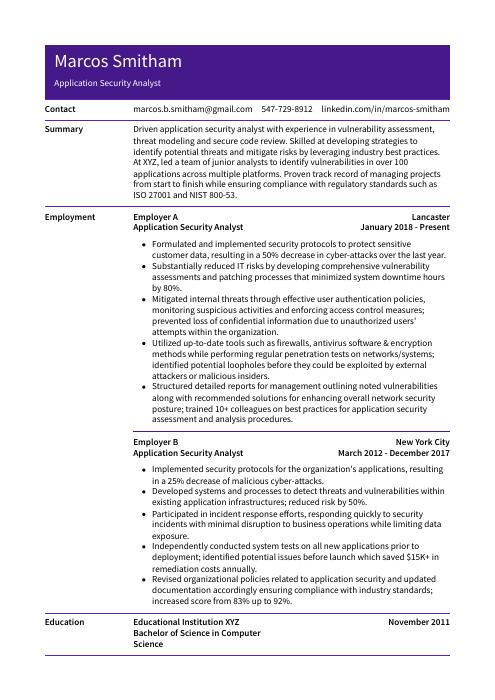 Pika
Pika Echidna
Echidna Fossa
Fossa Lorikeet
Lorikeet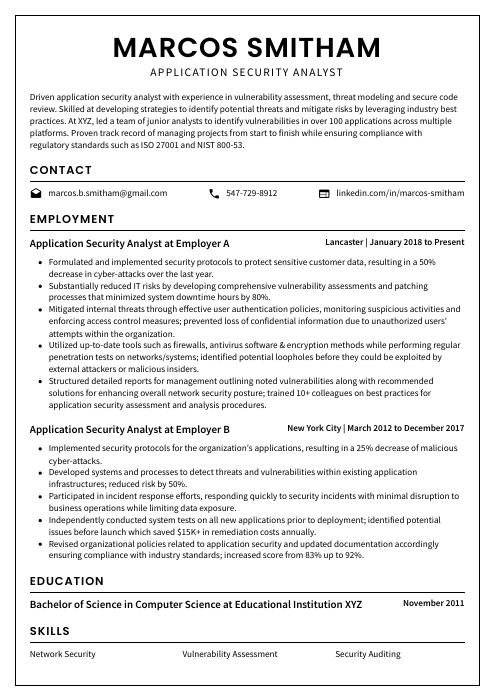 Cormorant
Cormorant Gharial
Gharial Rezjumei
Rezjumei