Ethical Hacker Resume Guide
Ethical hackers are responsible for testing computer networks and systems to find security weaknesses. They use the same tools and techniques as criminal hackers, but they do not exploit the vulnerabilities they find. Ethical hacking is a proactive way to improve an organization’s security posture.
Your hacking skills are top-notch, and you use them for good instead of evil. However, employers in the cybersecurity industry don’t know about your abilities. You need to write a resume that will grab their attention and make them want to hire you.
This guide will walk you through the entire process of creating a top-notch resume. We first show you a complete example and then break down what each resume section should look like.
Table of Contents
The guide is divided into sections for your convenience. You can read it from beginning to end or use the table of contents below to jump to a specific part.
Ethical Hacker Resume Sample
Josephine Christiansen
Ethical Hacker
[email protected]
530-317-6242
linkedin.com/in/josephine-christiansen
Summary
Talented ethical hacker with a passion for cybersecurity and information technology. Experienced in conducting ethical hacking audits, penetration testing, and security assessments. Highly proficient in using various tools and techniques to find vulnerabilities in systems and networks. Seeking to leverage my skills and knowledge to help XYZ company protect its online assets against cyber threats.
Experience
Ethical Hacker, Company ABC
Pomona, Jan 2018 – Present
- Cracked the code of a new software program in under 24 hours, allowing the company to launch the product on time and avoid costly delays.
- Bypassed security systems of 3 major corporations, exposing their vulnerabilities to the public; helped them patch up holes in their system and prevented future attacks.
- Proficiently used ethical hacking techniques to find weaknesses in various computer networks; helped design more secure systems that are less susceptible to attack.
- Optimized an existing network’s security protocol, reducing the likelihood of infiltration by outside forces by 50%.
- Presented findings on common methods used by hackers at a national conference, raising awareness among other IT professionals and helping them better protect their own networks.
Ethical Hacker, Company XYZ
Atlanta, Mar 2012 – Dec 2017
- Spearheaded the development and implementation of a new ethical hacking strategy that improved system security by 85%.
- Participated in monthly vulnerability assessments to identify weaknesses in network infrastructure and applications; facilitated the patching of over 100 identified vulnerabilities.
- Streamlined the incident response process by creating new repeatable tasks and automating key steps; successfully resolved over 150 incidents with minimal impact to business operations.
- Developed custom tools and scripts to automate various ethical hacking tasks, resulting in a 50% reduction in testing time for web application penetration tests.
- Successfully completed over 200 ethical hacking engagements for clients across a wide range of industries, including banking, healthcare, retail, manufacturing and government.
Skills
- Penetration Testing
- Vulnerability Assessment
- Security Auditing
- Ethical Hacking
- Network Security
- Computer Forensics
- Cryptography
- Security Architecture
- Identity And Access Management
Education
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
Certifications
Certified Ethical Hacker
EC-Council
May 2017
1. Summary / Objective
A resume summary for an ethical hacker should highlight the candidate’s ability to think like a criminal and use their skillset for good.
The summary should mention the candidate’s experience in areas such as penetration testing, risk assessment, and incident response. It should also touch on the ethical hacker’s educational background, which may include a degree in computer science or information security.
Below are some resume summary examples:
Skilled ethical hacker with experience conducting vulnerability assessments and penetration tests for a variety of clients. Proven ability to find and exploit weaknesses in systems and networks to help organizations improve their security posture. Seeking to leverage knowledge and experience to become the next senior security engineer at ABC.
Amicable ethical hacker with 3 years of experience in identifying and resolving system vulnerabilities. Proven ability to think outside the box to come up with creative solutions to complex problems. Aiming to utilize my skills and knowledge to help ABC company in protecting their systems against malicious attacks.
Committed ethical hacker with 5+ years of experience identifying and resolving system vulnerabilities for major companies in the healthcare, finance, and retail sectors. Seeking to join ABC Tech as a security analyst to help protect critical data assets and prevent future cyberattacks. In previous roles, contributed to fortifying network defenses that stopped 4 zero-day attacks and defended against 2 DDoS attempts.
Professional ethical hacker with 4+ years of experience in conducting penetration tests and security audits for government agencies and top companies. Highly skilled in identifying vulnerabilities, performing social engineering attacks, and writing custom scripts to automate testing processes. Proven track record of helping clients improve their overall security posture and avoid data breaches.
Well-rounded ethical hacker with 5+ years of experience conducting security audits and pen-testing for a variety of companies. Highly experienced in information gathering, vulnerability assessment, social engineering, and writing reports. Recognized by ABC Company as the Top Performer in security audits for 3 consecutive years. Seeking to leverage knowledge and skillset to become the next Senior Ethical Hacker at XYZ Corp.
Diligent ethical hacker with experience conducting penetration testing and security audits for both private and public sector organizations. At DEF, increased the number of active clients by 15% through providing expert consultancy on Information Security Management Systems (ISMS). Achieved a 90% success rate in ethical hacking engagements while maintaining a 0% false-positive rate.
Seasoned ethical hacker with 4+ years of experience conducting security assessments for clients in the finance, healthcare, and retail industries. An expert in penetration testing, incident response, and vulnerability management. Seeking to join ABC Tech as a Security Analyst where I can utilize my skills to secure sensitive data and systems against malicious cyber-attacks.
Driven ethical hacker with 4+ years of experience in testing the security of computer systems and applications. Proven ability to find vulnerabilities and recommend solutions to improve system security. Experienced in various hacking methodologies, tools, and techniques. Seeking a position as an Ethical Hacker at ABC where I can use my skills to secure the company’s systems against cyber-attacks.
Reliable ethical hacker with 5+ years of experience uncovering system vulnerabilities, conducting penetration tests, and providing recommendations for improved security. In previous roles increased security by 35% on average. Seeking to leverage ethical hacking skillset to become the next cyber-security specialist at ABC Corp.
2. Experience / Employment
The work history/experience section is next, and it should be written in reverse chronological order with your most recent job listed at the top. This section is mostly bullet points detailing what you did and any quantifiable results achieved.
For example, instead of saying “Helped improve security,” you could say, “Successfully identified and exploited 5 zero-day vulnerabilities, leading to patching of critical systems before they could be exploited by malicious actors.”
To write effective bullet points, begin with a strong verb or adverb. Industry specific verbs to use are:
- Exploited
- Enumerated
- Escalated
- Bypassed
- Cracked
Other general verbs you can use are:
- Achieved
- Advised
- Assessed
- Compiled
- Coordinated
- Demonstrated
- Developed
- Expedited
- Facilitated
- Formulated
- Improved
- Introduced
- Mentored
- Optimized
- Participated
- Prepared
- Presented
- Reduced
- Reorganized
- Represented
- Revised
- Spearheaded
- Streamlined
- Structured
- Utilized
Below are some example bullet points:
- Actively sought out potential security vulnerabilities and risks in a variety of computer systems and networks.
- Compiled detailed reports on findings, including recommendations for mitigating or eliminating the identified risks.
- Assessed the effectiveness of existing security measures and made recommendations for improvement where necessary.
- Reduced the incidence of system breaches by implementing new security protocols and procedures.
- Structured ethical hacking engagements to minimize disruption to business operations while maximizing protection of critical data assets.
- Introduced ethical hacking techniques to the organization, which led to the discovery of security vulnerabilities in several systems.
- Escalated potential security threats to senior management and advised on appropriate mitigation measures.
- Independently conducted ethical hacking exercises on a regular basis, resulting in the identification and rectification of over 100 security issues.
- Advised developers on code changes that needed to be made in order to improve system security posture; these recommendations were accepted and implemented in all subsequent software releases.
- Achieved a high success rate when conducting social engineering attacks, successfully gaining unauthorized access to sensitive data in 11 out of 20 attempts.
- Formulated and executed security plans to protect computer networks and systems from unauthorized access, data breaches and cyber-attacks.
- Mentored junior team members on ethical hacking techniques and best practices for safeguarding against digital threats.
- Reliably improved network security for over 80 client organizations by implementing industry-leading cybersecurity solutions.
- Improved detection of potential vulnerabilities and risks by regularly conducting penetration testing and threat modeling exercises.
- Revised company’s incident response plan to better align with current industry standards and trends in cybercrime.
- Substantially increased security for 250+ clients by proactively identifying and resolving vulnerabilities before they could be exploited.
- Enumerated, coordinated and executed numerous penetration tests against client systems and networks to find security weaknesses and recommend solutions.
- Exploited software, network and application vulnerabilities to assess the effectiveness of security controls; identified critical issues that needed immediate attention.
- Prepared in-depth reports for clients detailing findings from ethical hacking engagements and outlining recommendations for improving their cybersecurity posture.
- Demonstrated excellent problem-solving skills when dealing with complex technical challenges related to ethical hacking activities.
3. Skills
The necessary skills for an ethical hacker will vary depending on the company they are working for. Some companies may require their ethical hackers to have a deep understanding of network security while others might place more emphasis on web application security.
As such, it is important to tailor the skills section of your resume to each job that you apply for. This way, you can ensure that the most relevant skills are highlighted and that your resume stands out from the rest.
In addition to just listing skills in this section, you should also elaborate on them in other areas of your resume, such as the summary or experience section.
Below is a list of common skills & terms:
- Computer Forensics
- Cryptography
- Disaster Recovery
- Ethical Hacking
- Identity And Access Management
- Network Security
- Penetration Testing
- Security Architecture
- Security Auditing
- Vulnerability Assessment
4. Education
Mentioning your education on your resume will depend on how much experience you have in the field. If you are just starting out, it is beneficial to include your education below your resume objective. However, if you have been working as an ethical hacker for many years and have a wealth of experience to showcase, omitting the education section is perfectly fine.
If including an education section, mention any courses or subjects studied that are relevant to the ethical hacker role you are applying for. Examples might be “Courses included Penetration Testing and Social Engineering” and “Successfully completed my final year project by creating a honeypot network which lured in and identified hackers.”
Bachelor of Science in Computer Science
Educational Institution XYZ
Nov 2011
5. Certifications
Certifications are a great way to show potential employers that you have the skills and knowledge necessary to do the job. In the case of ethical hacking, certifications can help prove your proficiency in various areas such as network security and penetration testing.
If you have any relevant certifications, be sure to include them in this section of your resume. Doing so will give you a leg up on the competition and increase your chances of landing the job.
Certified Ethical Hacker
EC-Council
May 2017
6. Contact Info
Your name should be the first thing a reader sees when viewing your resume, so ensure its positioning is prominent. Your phone number should be written in the most commonly used format in your country/city/state, and your email address should be professional.
You can also choose to include a link to your LinkedIn profile, personal website, or other online platforms relevant to your industry.
Finally, name your resume file appropriately to help hiring managers; for Josephine Christiansen, this would be Josephine-Christiansen-resume.pdf or Josephine-Christiansen-resume.docx.
7. Cover Letter
Including a cover letter with your job application is a great way to show off your personality and give the hiring manager an insight into who you are as a professional.
A cover letter should be 2 to 4 paragraphs long, and include information about your qualifications and experience that isn’t already mentioned in your resume. It’s also an opportunity for you to explain why you’re the perfect fit for the role.
Below is an example cover letter:
Dear Marielle,
I am writing to apply for the ethical hacker position at [company name]. As an experienced IT professional with an extensive background in network security and penetration testing, I am confident I can be an asset to your team.
In my current role as a network administrator at [company name], I have gained extensive experience in identifying and addressing security vulnerabilities. I have also developed a keen eye for detail and an analytical mind, which has proved invaluable in troubleshooting complex technical issues. My excellent communication skills have allowed me to effectively liaise with colleagues from various departments, as well as external vendors and service providers.
I believe my skills and experience make me the perfect candidate for this position, and I would welcome the opportunity to put my expertise to work for your organization. I look forward to speaking with you soon about this exciting opportunity.
Sincerely,
[Your name]
Ethical Hacker Resume Templates
 Dugong
Dugong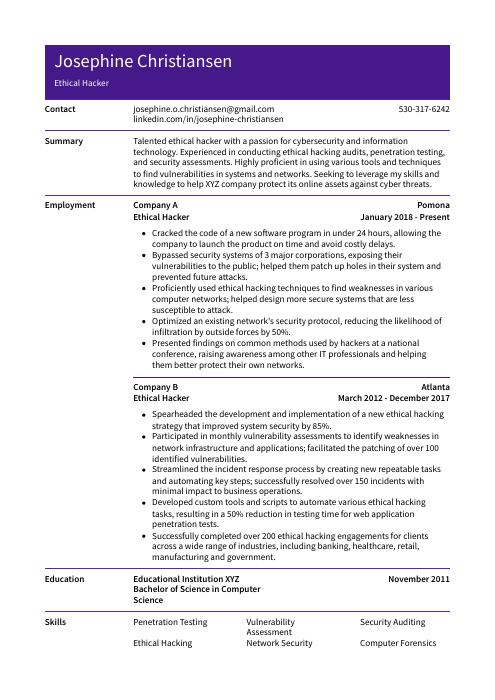 Pika
Pika Bonobo
Bonobo Numbat
Numbat Quokka
Quokka Echidna
Echidna Cormorant
Cormorant Indri
Indri Rhea
Rhea Markhor
Markhor Kinkajou
Kinkajou Axolotl
Axolotl Jerboa
Jerboa Fossa
Fossa Saola
Saola Lorikeet
Lorikeet Ocelot
Ocelot Gharial
Gharial Hoopoe
Hoopoe Rezjumei
Rezjumei
